Currently our highest voted Uservoice idea is to add support for Linux deployments in Octopus. We are going to implement this by adding first-class support for servers running SSH that will map very closely to the way that Windows deployments with Octopus work today.

For the purpose of this we will be introducing a new term in Octopus, agentless machines. An agentless machine will not be running a Tentacle, instead it will use a different method of communication, e.g. SSH.
Our goal with this RFC is to make sure that the way we implement this feature will be suitable for the widest range of customers.
Introducing agentless machines
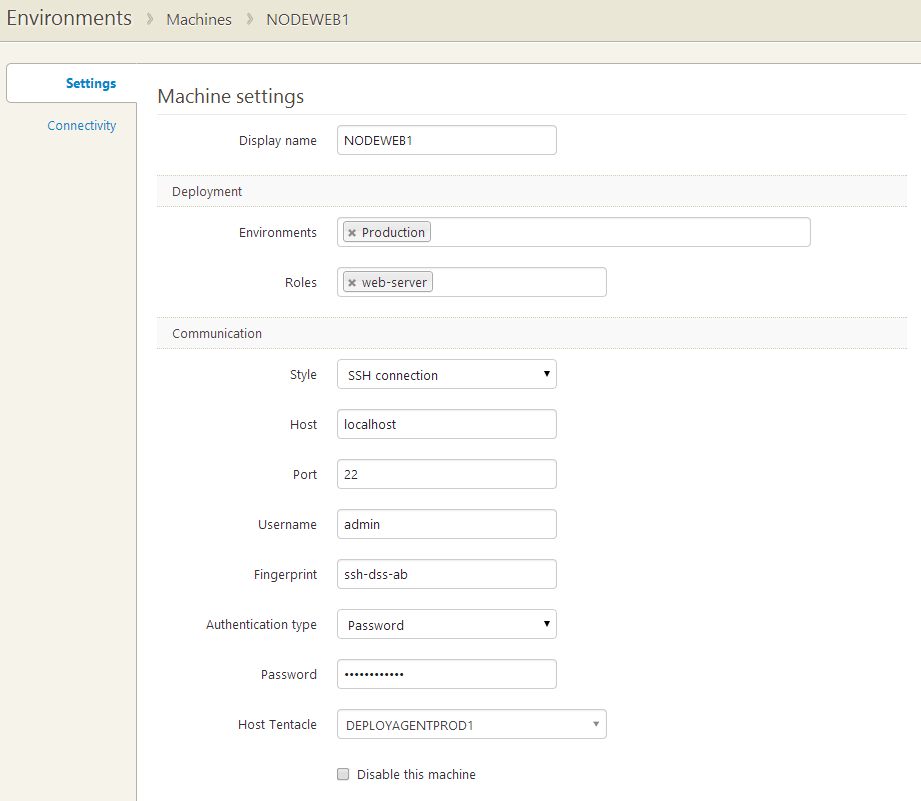
Setting up a new agentless machine, e.g. a Linux server running SSH, in Octopus will work the same way as when adding a new machine running a Tentacle.
Adding an agentless machine
Agentless machines are configured by choosing SSH rather than Listening or Polling as the communication style.
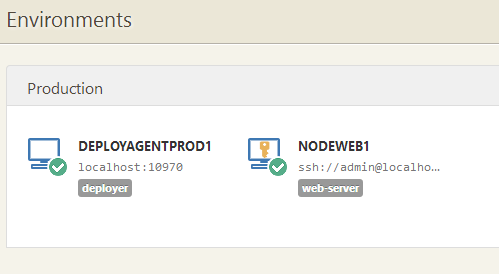
Environment with an agentless machine
Agentless machines appear on the Environments page just like regular Tentacles, showing their location and status (online/offline)
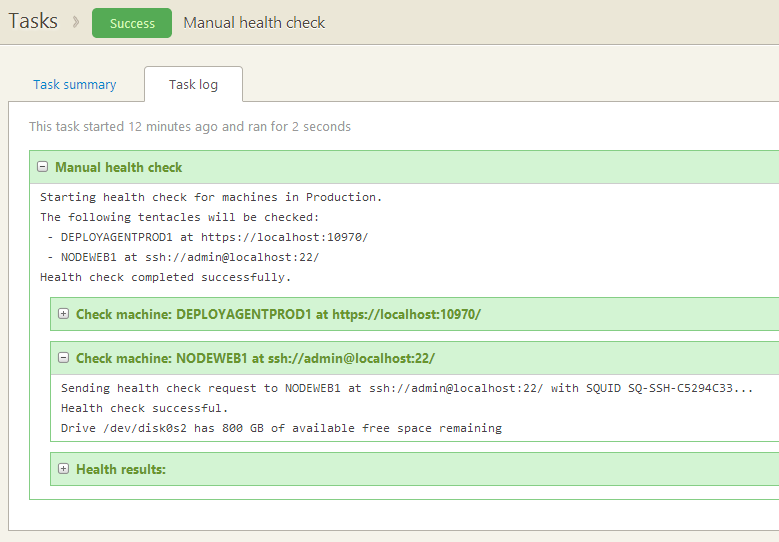
Health checking an agentless machine
Typical Octopus tasks like heath checks, ad-hoc scripts and so-on run across all appropriate machines, including both Tentacle and agentless machines if both styles are being used.
Authentication
Our aim is to support the following authentication types for the SSH target machines
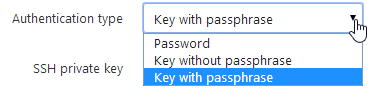
Password
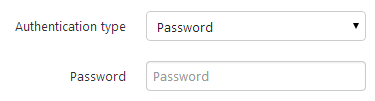
Key without passphrase
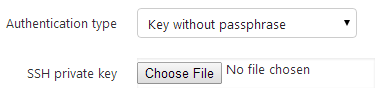
Key with passphrase
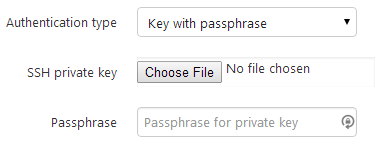
Private keys will be stored in the Octopus database as encrypted properties.
Network topology
Connections to agentless machines won’t be made directly from the Octopus Server; instead, one or more Tentacles will be used to make outbound connections to the machine. We’re planning to add a hidden, “shadow” Tentacle running in a low-privilege process on the Octopus Server itself as a convenient default, but using specific Tentacles to handle different network topologies is also a feature we’re considering.
Octopus footprint on agentless machines
Octopus will upload compressed packages to the target machine before any deployment takes place, so we require some local storage on the target machine that will go to ~/.tentacle/. We will also extract the packages to a default location like we do on a Tentacle machine, e.g. ~/.tentacle/apps/{environment}/{project}/{package}/{version}, and we will also support custom installation locations to move the files elsewhere.
Package acquisition
Because a Tentacle machine is required for doing SSH deployments the package acquisition for these deployments will change slightly from the way Windows deployments with Octopus work today.
The Tentacle machine will extract the NuGet package and create a .tar.gz tarball that then will be uploaded to the target machines.
The Tentacle machine can be co-located with the target machines to optimize bandwidth usage, i.e. Octopus uploads the package to the Tentacle, which in turn will send the package to the target machines.
Deployment
Package deployment steps will run entirely via a single shell session on the target machine.
- We will check and ensure the Octopus scripts are up-to-date
- Package and supporting deployment files will be uploaded via SCP
- Deployment orchestration script will be executed
- Default installation directory will be created if it doesn’t exist
- tar file will be unpacked
predeploywill run- If a custom installation directory has been specified
- If the option to purge the directory before deployment is true, we purge the custom installation directory
- Copy the extracted files to the custom directory
deploywill runpostdeploywill run- Run retention policies to clean up old deployments
- Delete the Octopus variables file (to ensure sensitive variables aren’t left on the server)
Deployment scripts
The main deployment orchestration script will be written in bash, as this is the least common denominator amongst *nix distributions. This script will look for predeploy/deploy/postdeploy scripts, that can be created by the user, and execute them if they are present.
The predeploy/deploy/postdeploy scripts can be written in the users preferred scripting language (but the user would have to ensure that it is installed on the server that the deployment is run on).
predeploy- tasks required to be run pre deployment, e.g. config transformations needed for your application.
deploy- tasks required for the actual deployment of your application.
postdeploy- tasks required to be run post deployment. e.g. clean up any temp files created during the deployment of your application.
The working directory will be the default installation directory for the predeploy script, and either the default or custom installation directory for the deploy and postdeploy scripts.
Environment variables for deployments
Octopus has a more sophisticated variable system and syntax than Linux environment variables can support. Having to map between names like Octopus.Action[Install website].Status.Code and valid POSIX equivalents seems uncomfortable and error-prone. Large Octopus deployments also tend to carry a lot of variables, so we’re uneasy about dumping these arbitrarily into the environment in which the deployment script runs.
Instead of setting environment vars directly, deployment scripts will have access to a tentacle command that can be used to retrieve values that they require. E.g. to retrieve the custom installation directory used by the deployment the user can call the tentacle command like so:
DEST=$(tentacle get Octopus.Action.Package.CustomInstallationDirectory)
This declares an environment variable DEST to hold the custom installation directory (subsequently available to the script as $DEST).
Values with embedded spaces and so-on can be supported using " quotes.
Though we’re unlikely to implement it in the first version of the command, we’re considering some more sophisticated features like iteration:
for ACTION in $(tentacle get "Octopus.Action[*]")
do
echo "The status of $ACTION was $(tentacle get "Octopus.Action[$ACTION].Status.Code")"
done
This highlights the kinds of opportunities we see to make writing deployment scripts more enjoyable.
Other features of the tentacle command
Using the tentacle helper will also provide consistent access to the commands supported using PowerShell cmdlets on Windows machines.
Setting output variables
Output variables can be sent to the Octopus server using tentacle set:
tentacle set ActiveUsers 3
Or:
ps -af | tentacle set RunningProcesses
Collecting artifacts
Files from the target machine can be collected as Octopus artifacts using tentacle collect:
tentacle collect InstallLog.txt
Running tools
Where we (or others) provide helper scripts that themselves need access to variables, paths and so-on, these can be invoked using tentacle exec:
tentacle exec xmlconfig Web.config
Deployment features
Features like XML configuration transformations/appsettings support will run on the target machine.
Supporting Octopus scripts and executables will be part of the default folder structure on the target machine, i.e. ~/.tentacle/tools/, in this folder we can also include helper apps using Mono for supporting .NET-specific conventions like XML configuration transformation/appsettings.
We can also include different scripting/executable options to support other deployment features.
Retention policies
Once a deployment has completed, we will apply the retention policy that has been specified for the project, just like we do with Windows deployments.
The user can specify to keep a number of days worth of deployments, or a specific number of deployments. If either of these have been specified we will remove any files that do not fall within the specified retention policy.
System requirements
Linux distributions can vary significantly in their default configuration and available packages. We’re aiming to choose a widely-supported baseline that makes it possible to deploy with Octopus to practically any current Linux distribution.
The fundamental assumptions we will make about a target machine are:
- It’s accessible using SSH and SCP
- The user’s login shell is Bash 4+
taris available
The platforms that we ourselves plan to build and test against are:
- Amazon Linux AMI 2014.03
- Ubuntu Server 12.04 LTS
We will do our best to remain distro-agnostic, but if you’re able to choose one of these options for your own servers you’ll be helping us provide efficient testing and support.
Outstanding Questions
- Management of platform-specific paths
- where apps are being deployed to both Windows and Linux servers, paths like “Custom Installation Directory” will need to be specified separately for Linux and Windows. Can we make this experience better?
- Naming of the deploy scripts
- predeploy/deploy/postdeploy, or
- pre-deploy/deploy/post-deploy, or
- pre_deploy/deploy/post_deploy?
- Customization of paths where we will upload packages and extract packages by default
- is it necessary to configure this via Octopus, or can locations like
~/.tentacle/appsbe linked by an administrator to other locations as needed?
- is it necessary to configure this via Octopus, or can locations like
- Writing out variables like we do in PowerShell
- In PowerShell we first encrypt them with DPAPI, is there a similar standard crypto function available on Linux?
We need your help!
What we would really appreciate is for customers who are already using SSH in Octopus, or that would want to start using it, to give us feedback on our plan of how to implement SSH deployments in Octopus.
Whether it be improvements to the suggested implementation above or if we’ve made assumptions that just will not work, then please let us know in the comments below.