We pride ourselves on making Octopus Deploy a secure product. The security and integrity of your Octopus Deploy installation is the result of a partnership between us as the software vendor, and you as the host and administrators of your installation.
This section provides information about the responsibility we take to provide a secure software product, and considerations for you as the host and administrator of your Octopus Deploy installation.
Our Certifications
Octopus Deploy is compliant with cybersecurity standards such as ISO27001 & SOC II. Every year Octopus undergoes a security review conducted by a third-party company. We also run several public bug bounty programs to encourage the security community to help us keep our customers safer. We are an active member of MITRE through its CVE program as a CNA, meaning that we’re responsible for disclosing any vulnerabilities in our product to allow customers security teams to make informed decisions.
A comprehensive overview of our security controls is available in our Trust Centre where it is possible to request access to our certifications and penetration test reports, as well as other supporting documents and policies.
We often hear from customers who want to know more about our security posture. We’ve performed a self assessment against various industry-standard controls. Feel free to use this in any vendor assessments you need to perform.
Responsibility
Octopus Deploy has the responsibility of providing a secure and stable platform for managing your deployments.
You have the responsibility for how that platform is implemented and exposed to your infrastructure and users.
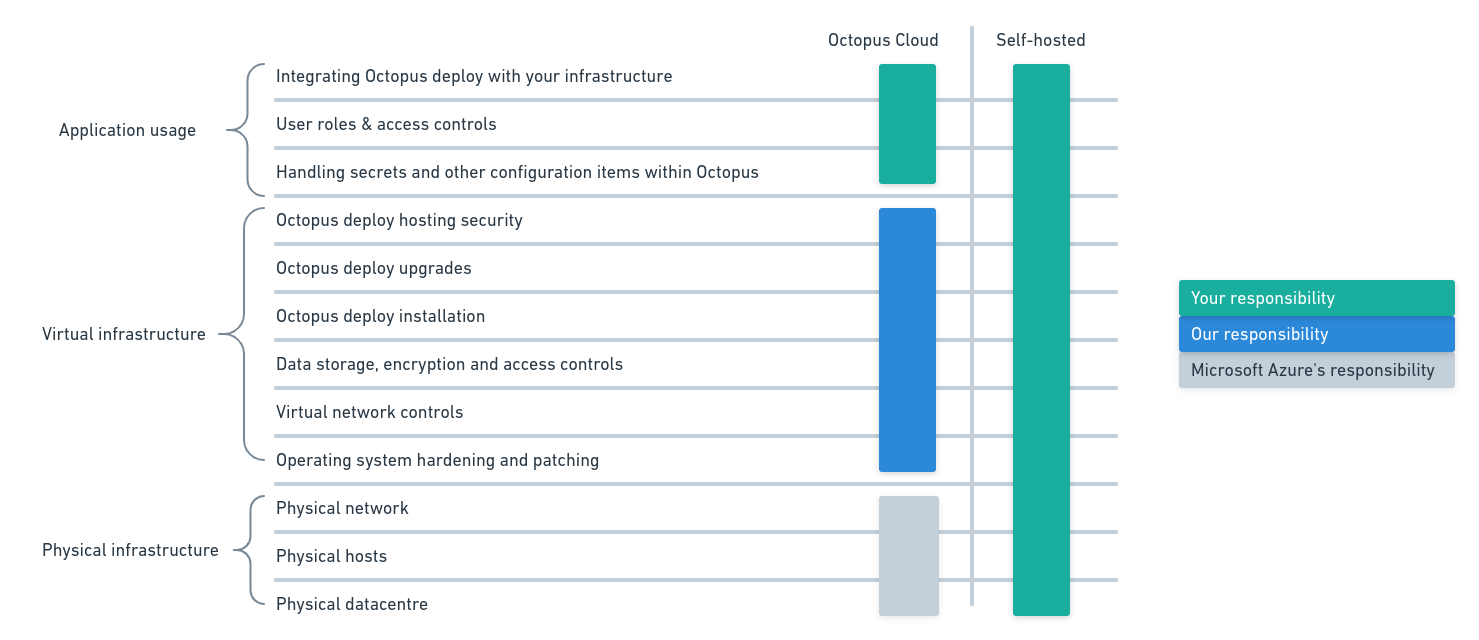
Octopus Cloud
If you are using Octopus Cloud, where we host your Octopus Server on your behalf, we take additional responsibility for the security and integrity of the Octopus Server. In this case, you are responsible for:
- How you connect Octopus to your infrastructure.
- How you identify your users and control their activities within Octopus.
- How you handle sensitive information within Octopus.
Self-hosted
If you are hosting the Octopus Server yourself, you take responsibility for the security and integrity of the Octopus Server. In this case, you also taking responsibility for:
- How you harden the underlying server operating system.
- How you protect the Octopus Server files on the operating system.
- How you store files generated by Octopus Server.
- How you secure your SQL Database and protect the data generated by Octopus Server.
- How you expose your Octopus Server to your infrastructure.
- How you identify your users and control their activities within Octopus.
- How you handle sensitive information within Octopus.
Built in to Octopus Deploy
Data encryption
Octopus Deploy encrypts any data which we deem to be sensitive. You can also instruct Octopus Deploy to encrypt sensitive variables which can be used as part of your deployments.
Learn about data encryption and sensitive variables.
Secure communication
Your Octopus Server communicates with the machines you configure as targets for your deployments using transport encryption and tamper proofing techniques.
Learn about secure communication.
Auditing
Arguably one of the most appreciated features in Octopus Deploy is our support for detailed auditing of important activity.
Learn about auditing.
Prevention of common vulnerabilities and exploits
To make Octopus Deploy useful to your organization it needs a high level of access to your servers and infrastructure. We take great care to understand common vulnerabilities and exploits which could affect your Octopus Deploy installation, and ensure our software prevents anyone from leveraging these.
FIPS compliance
We take every reasonable effort to make Octopus Server, Tentacle, Calamari, and any other tools we provide FIPS 140 compliant. If something is not FIPS 140 compliant we will take every reasonable effort to fix the problem, or otherwise degrade the feature gracefully.
Learn about FIPS and Octopus Deploy.
Provided by the host
The following sections describe the responsibilities taken by whomever is hosting your Octopus Server. If you are using Octopus Cloud, that’s us. If you are self-hosting, this is you.
Safely exposing your Octopus Deploy installation
In many scenarios you will want to expose parts of your Octopus Deploy installation to external networks. You should take care to understand the security implications of exposing your Octopus Deploy installation, and how to configure it correctly to prevent unwanted guests from accessing or interfering in your deployments.
Learn about safely exposing Octopus Deploy.
Safely executing scripts on the Octopus Server
To make Octopus as useful as possible after installation, you can perform many kinds of deployments without setting up other infrastructure. We achieve this using a concept called a worker, and in a default installation, this is called the built-in worker. Depending on your scenario, this can have a big impact on the security and integrity of your Octopus Server.
Learn about configuring workers.
Provided by your Octopus administrators
The following sections describe the security controls you can put in place when managing your Octopus Server regardless of where it is hosted.
Identity and access control
Before a person can access your Octopus Deploy installation, they must validate their identity. We provide built-in support for the most commonly used authentication providers including Active Directory (NTLM and Kerberos), Google Apps, and Microsoft Azure Active Directory. Octopus Deploy works natively with Open ID Connect (OIDC) so you can connect to other identity providers. If you don’t want to use an external identity provider, you can let Octopus Deploy securely manage your usernames and passwords for you.
Learn about authentication providers.
Once a person has verified their identity, you can control which activities these users can perform.
Learn about managing users and teams.
HTTP security headers
You can configure the Octopus Server to send certain standard HTTP security headers with each HTTP response. The Octopus Server will be secure by default, however you can enable certain advanced HTTP security headers, like HSTS if you desire.
Learn about HTTP security headers.
PCI/DSS compliance
We have a lot of customers running Octopus Deploy in their PCI-compliant environments. We don’t claim to be experts in PCI compliance, especially since every situation is slightly different. What we can do is offer some recommendations primarily focused on your use of Octopus Deploy and different models you can achieve with it.
Learn about PCI/DSS compliance and Octopus Deploy.
Outbound requests
Some components in Octopus Deploy will make outbound requests from time to time. Generally these requests are required to perform your deployments, some of them are for things like certificate revocation checks, and some are designed to help us build a better product for you.
Learn about the outbound requests made by Octopus Deploy.
Privacy
Learn about our privacy policy. We are currently preparing for the General Data Protection Regulation (GDPR) to be ready ahead of the 25 May 2018 enforcement date.
Security disclosure policy
No software is ever bug free, and as such, there will occasionally be security issues. Once we have fixed a verified security vulnerability we follow a practice of responsible disclosure. You can view the entire list of disclosed security vulnerabilities in the MITRE CVE database.
Learn about our security disclosure policy.
Contact us
If you have a concern regarding security with Octopus Deploy, or would like to report a security vulnerability, please send an email to security@octopus.com.
For security vulnerabilities, please include as much information as possible, with full details about how to reproduce and validate the vulnerability, preferably with a proof of concept. If you wish to encrypt your report, please use our PGP key. Please give us a reasonable amount of time to correct the issue, before making it public.
We will respond to your report within one business day.
Help us continuously improve
Please let us know if you have any feedback about this page.
Page updated on Tuesday, April 16, 2024