As part of your deployment, Octopus also captures the Kubernetes manifests that were applied to the cluster. This allows you to validate and verify the exact manifests that were applied, allowing for easier debugging of any issues.
Octopus will show a list of all the applied manifests on a deployment screen — the Applied Manifests view on the KUBERNETES tab.
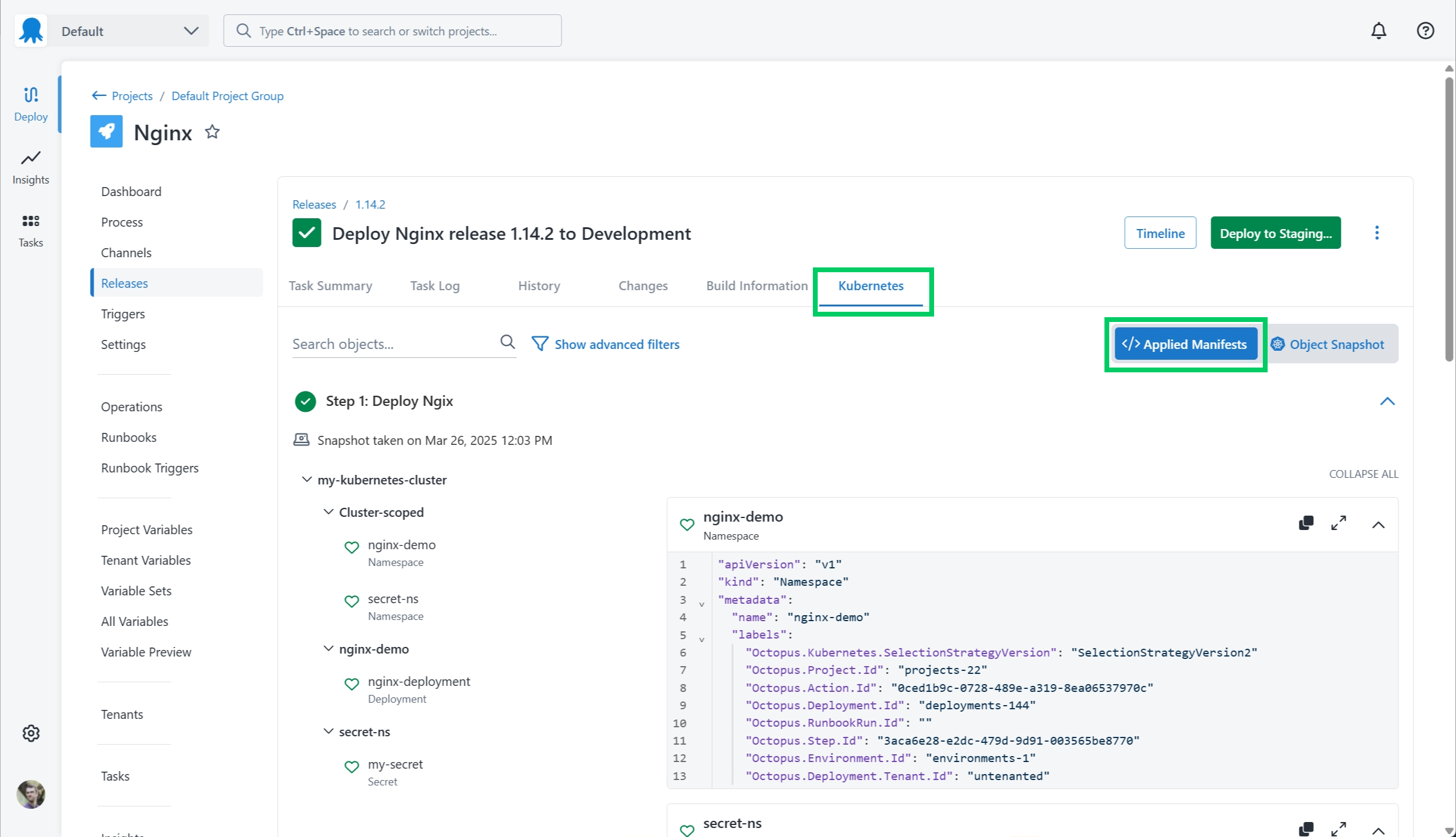
Where it is available
Applied manifests are available for these steps.
- Deploy Kubernetes YAML
- Deploy a Helm Chart
- Deploy with Kustomize
- Configure and apply Kubernetes resources (except for the Blue/Green deployment strategy)
- Configure and apply a Kubernetes ConfigMap
- Configure and apply a Kubernetes Secret
- Configure and apply a Kubernetes Ingress
- Configure and apply a Kubernetes Service
How it works
When Octopus performs a Kubernetes deployment step, the individual manifests are captured, encrypted and stored on the filesystem. If the input manifest contained multiple resources in a single file, these are broken out into individual manifests for viewing.
If the deployment step is a Helm deployment, Octopus retrieves the templated manifests generated by Helm and displays the result.
How to use
For each step that performs a Kubernetes deployment, there is a navigation tree with all the manifests listed under their deployment target and in their deployed namespace. For non-namespaced resources, they are listed under the Cluster-scoped node.
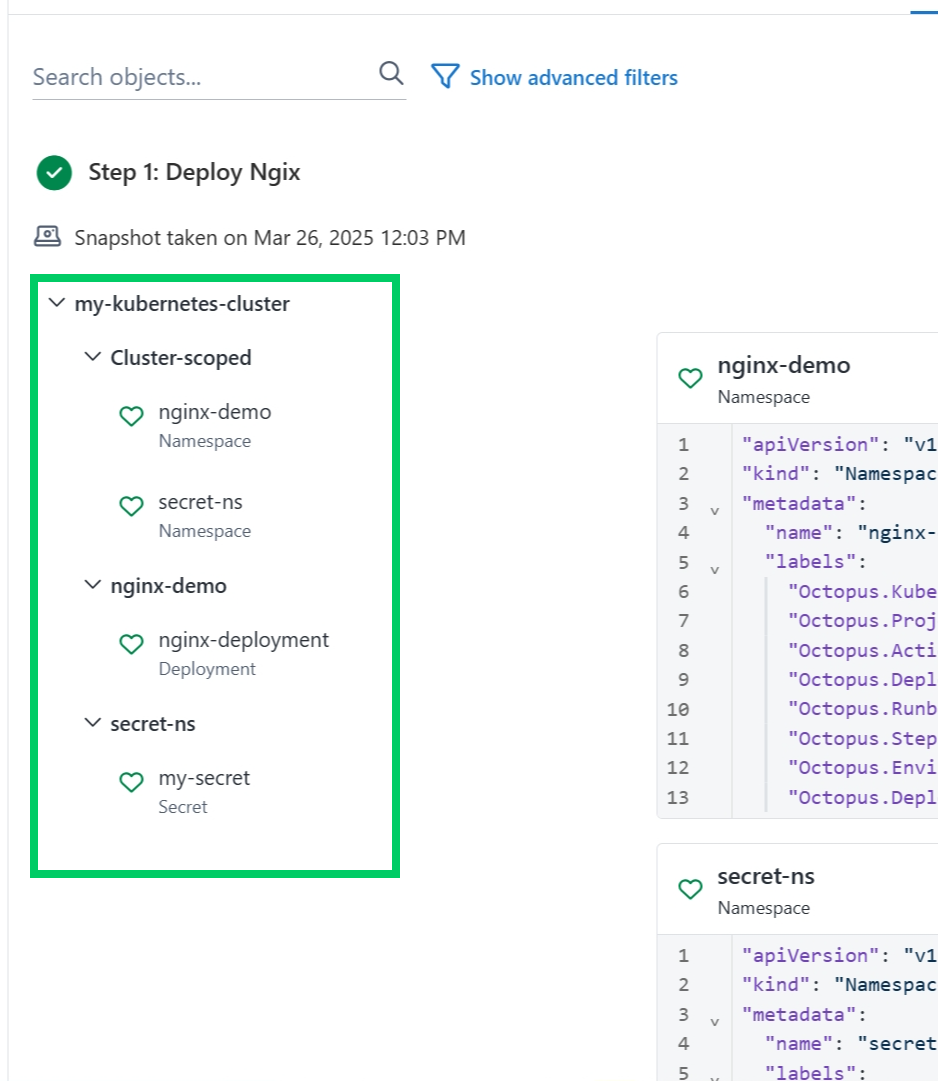
If Step Verification is enabled, an icon indicating the health of the resource is shown on the resource. See here for more information.
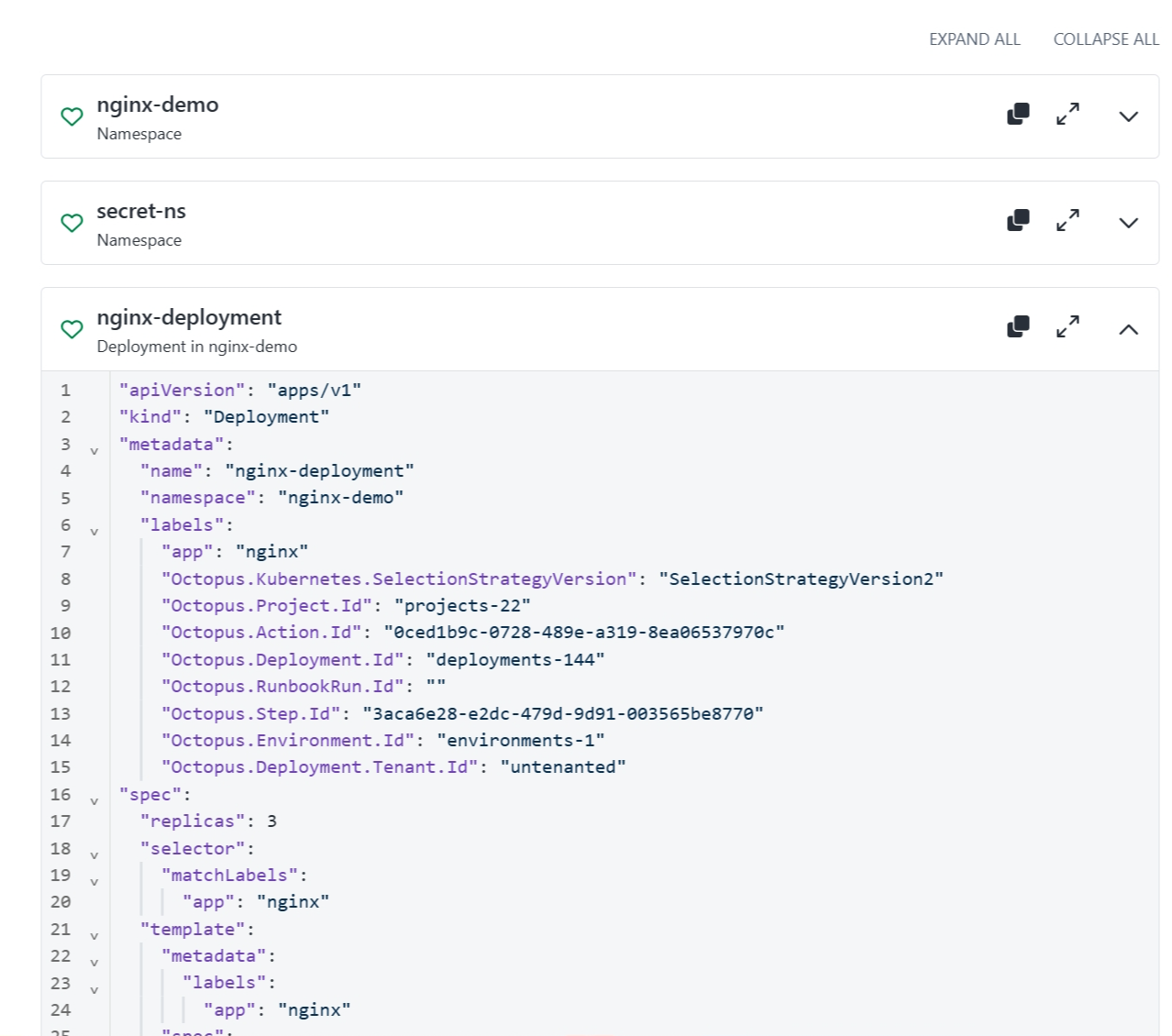
On the right-hand side, the individual manifests are displayed in collapsible sections.
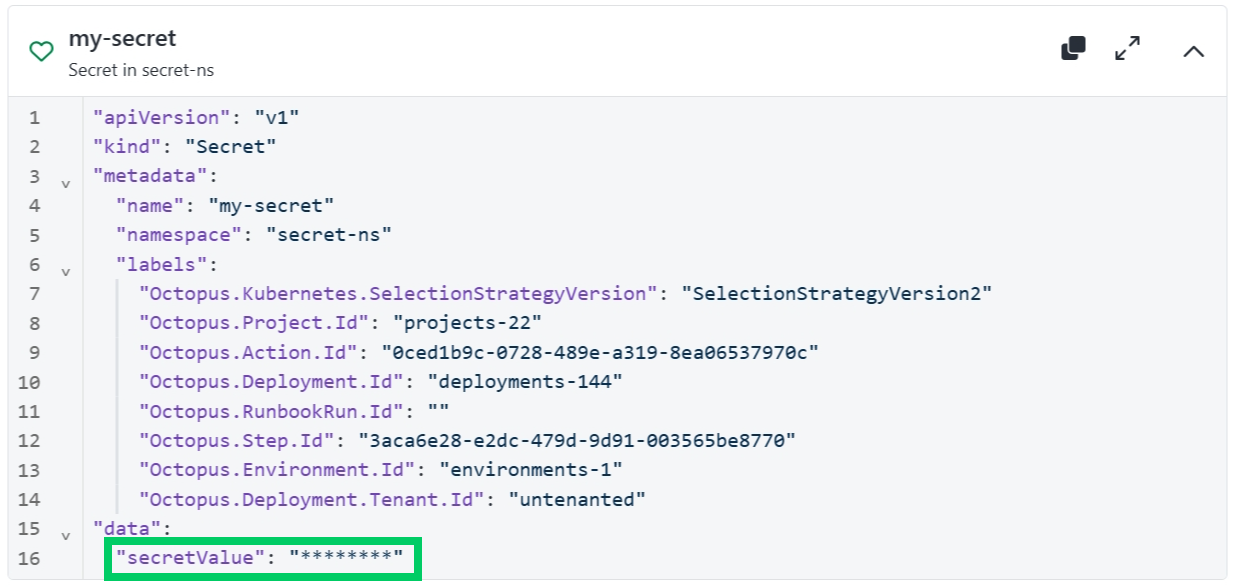
Kubernetes Secret resources and Octopus sensitive variables
To protect your Octopus sensitive values, Octopus will obfuscate these values if they are substituted into when displaying the manifest. For Kubernetes Secrets, we obfuscate all values regardless of whether they came from Octopus sensitive variables or other sources.
It is highly recommended when using variable substitution to add Octopus sensitive variables to your manifests that you store these variables in Kubernetes Secret resources.
You can correctly base64 format the sensitive variable using the following syntax:
#{ MySensitiveValue | ToBase64 }
Help us continuously improve
Please let us know if you have any feedback about this page.
Page updated on Tuesday, March 25, 2025