Microsoft Azure provides a Docker image registry known as Azure Container Registry.
Configuring an Azure Container Registry
Select Azure Container Registry from the Azure marketplace and select create to create a new registry.
Provide the unique registry name that all your repositories (packages) will be stored in.
Make sure you select Enable under the Admin user option. This is what will expose the credentials that are needed by Octopus to connect to the API.
Azure Container Registries can be configured as an external feed in Octopus by navigating to Deploy ➜ Manage ➜ External Feeds and adding an new feed of type Azure Container Registry.
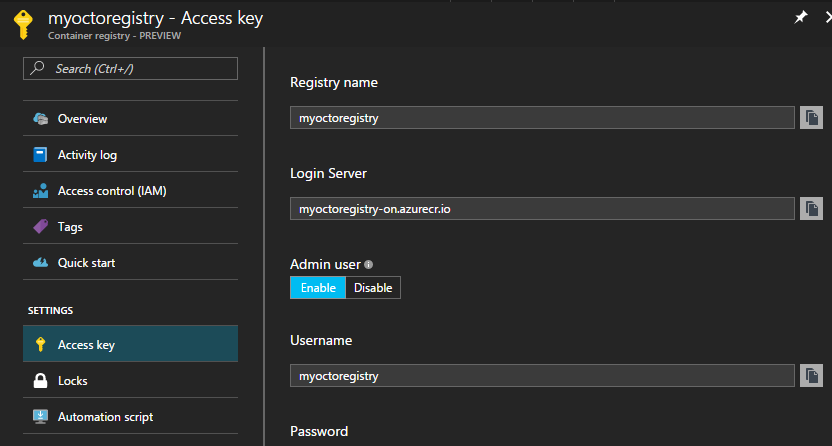
Once the service has been provisioned, go to the Container Registry details and load the Access Key blade. The login server indicates the HTTPS url that needs to be supplied into the Octopus Registry feed. In the case above this will be https:\\myoctoregistry-on.azurecr.io.
With the Admin user toggle enabled, you will be provided with username and password credentials, these will needed these when you create the Octopus Deploy feed. The password can be regenerated at any time so long as you keep your Octopus instance updated with the new credentials.
Adding an Azure Container Registry as an Octopus External Feed
Create a new Octopus Feed (Deploy ➜ Manage ➜ External Feeds) and select the Azure Container Registry Feed type. With this selected you will need to provide the username and password credentials configured above.
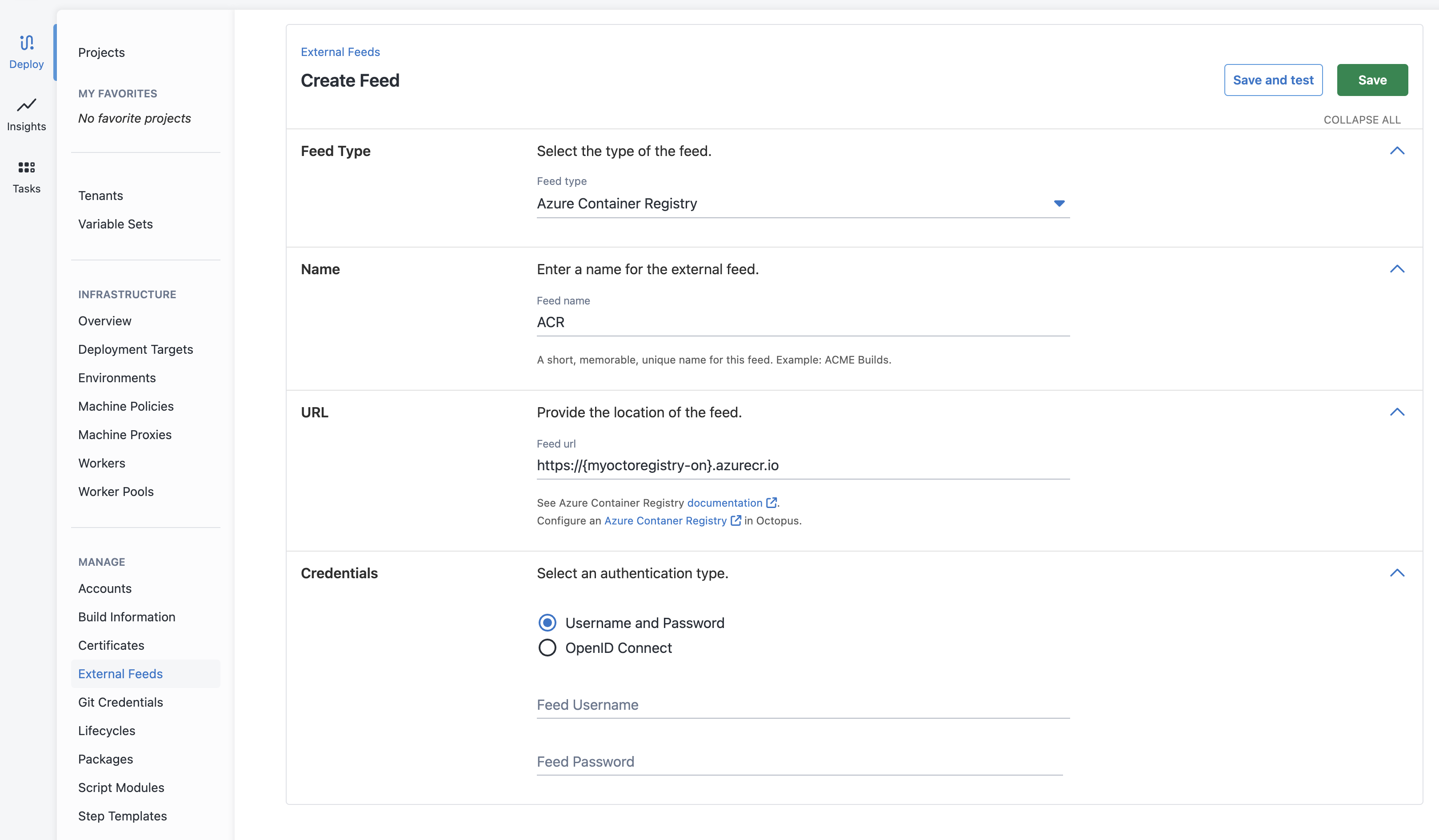
Save and test your registry to ensure that the connection is authorized successfully.
Adding an Azure Container Registry with OpenID Connect as an Octopus External Feed
Octopus Server 2025.2 adds support for OpenID Connect to ACR feeds. To use OpenID Connect authentication you have to follow the required minimum configuration.
Before creating an OpenID Connect Azure Container Registry feed, you will need an Microsoft Entra ID App Registration and a Federated Credential.
If you do not currently have an Microsoft Entra ID App Registration follow the App Registration guide.
To manually create a Federated Credential follow the Add a federated credential section in the Microsoft Entra ID documentation. The federated credential will need the Issuer value set to the configured Octopus Server URI. This URI must be publicly available and the value must not have a trailing slash (/). For example https://samples.octopus.app. For more information on configuring external identity providers see Configure an app to trust an external identity provider.
Create a new Octopus Feed (Deploy ➜ Manage ➜ External Feeds) and select the Azure Container Registry Feed type. With this selected you will need choose OpenID Connect as the authentication type.
Add the following properties to the feed credentials:
- Client ID: {{The Azure Active Directory Application ID (Client ID)}}
- Tenant ID: {{The Azure Active Directory Tenant ID}}
- Subject: Please read OpenID Connect Subject Identifier for how to customize the Subject value
- Audience {{The audience set on the Federated Credential}} This can be set to the default of
api://AzureADTokenExchangeor a custom value if needed
At this time, OpenID Connect external feeds are not supported for use with Kubernetes containers. This is because the short-lived credentials they generate are not suitable for long-running workloads.
Help us continuously improve
Please let us know if you have any feedback about this page.
Page updated on Thursday, September 4, 2025