When specifying a connection string, it’s usually preferable to use Windows Authentication because you don’t need to put passwords in your Web.config file. However, this doesn’t work in every scenario, so if you have to use a password in your connection string then it’s a good idea to encrypt it. Step Templates are a great way to enhance the native capabilities of Octopus Deploy. So to make encrypting the connection string section easier, I created a new template to do just that.
You can grab the new IIS Website - Encrypt Web.Config Connection Strings from the Octopus Deploy Library. Under the covers, this template makes use of the aspnet_regiis tool in order to encrypt the Web.Config. Adding the step to your deployment process will take you do the step details page for configuration.
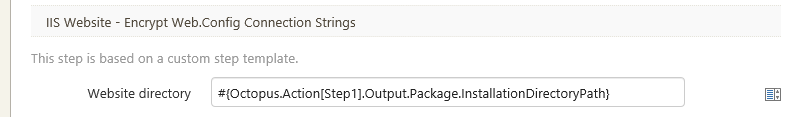
This template takes a single parameter called Website directory that you typically set to the InstallationDirectoryPath for the package deployment step. Note that you must specify the name of the package deployment step as part of the variable.
#{Octopus.Action[MyDeployPackageStep].Output.InstallationDirectoryPath}This step is designed to run after a package has been deployed to a web server. Unfortunately, this means that if you use the IIS web site and application pool feature, there is a slight window in which the Web.config will not be encrypted. To be completely safe, it would be ideal to apply the encryption before re-pointing IIS to the new Website. To work around this issue turn off the feature and use a custom PowerShell script to update IIS.
After you’ve added the step to your deployment process, your next deployment will have a nicely encrypted connection string section.