Like Octopus, Jenkins is just one step in your pipeline, complementing other systems and services.
You can connect Jenkins to most industry tools, securely storing their credentials, secrets, and API keys. By storing these login methods, Jenkins seamlessly connects to those other services during its automation processes.
Jenkins’ documentation recommends using the Credentials Binding plugin. It’s one of the installer-suggested plugins during the Jenkins setup, so it’s possible you already installed it (and used it) without realizing.
In this post, I walk you through how to install the plugin and the different ways it’s used.
How to install the Credentials Binding plugin
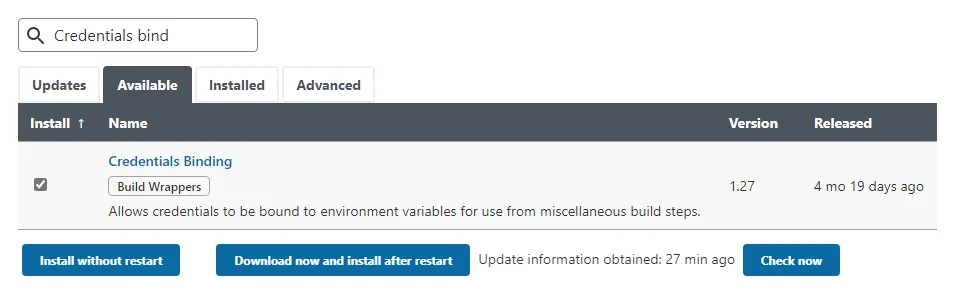
If you don’t have the Credentials Binding plugin installed, it’s easy to add:
- Click Manage Jenkins from the menu.
- Click Manage Plugins.
- Click the Available tab and start typing
Credentials Bindinginto the Filter field. The plugin should appear in the predicted search results. - Check the tick box to the left of the plugin then click Install without restart.
Jenkins installs the plugin and all dependencies, including other plugins and extensions.
The Credentials Binding plugin stores your authentication methods in 2 different ways:
Let’s look at the difference.
Global credentials
Global credentials are manually entered login methods stored in Jenkins. Anyone with access can use the credentials to connect to other services. These can include:
- Code repos, like GitHub or BitBucket
- Packaging services, like a Docker registry or TeamCity feed
- Deployment tools, like Octopus
How to add credentials in Jenkins
To add credentials in Jenkins:
- Click Manage Jenkins from the menu.
- Scroll down to the Security heading and click Manage Credentials.
- Click Jenkins under the Stores scoped to Jenkins heading.
- Click Global credentials (unrestricted) under the System heading.
- If no credentials exist, you can click the How about adding some credentials? link, otherwise click Add Credentials from the left.
- Select the type of credentials you want to store from the Kind field’s dropdown box, complete the fields and click OK. You can add the following types of credentials:
- Usernames and passwords
- SSH usernames and private keys
- Secret files
- Secret text
- Certificates
Regardless of the option you select, always enter a meaningful ID and Description.
Using global credentials in Jenkins
After you add the credentials, you can call on them to connect to other tools in your pipeline, whether that’s through the UI, a plugin, or a Jenkinsfile.
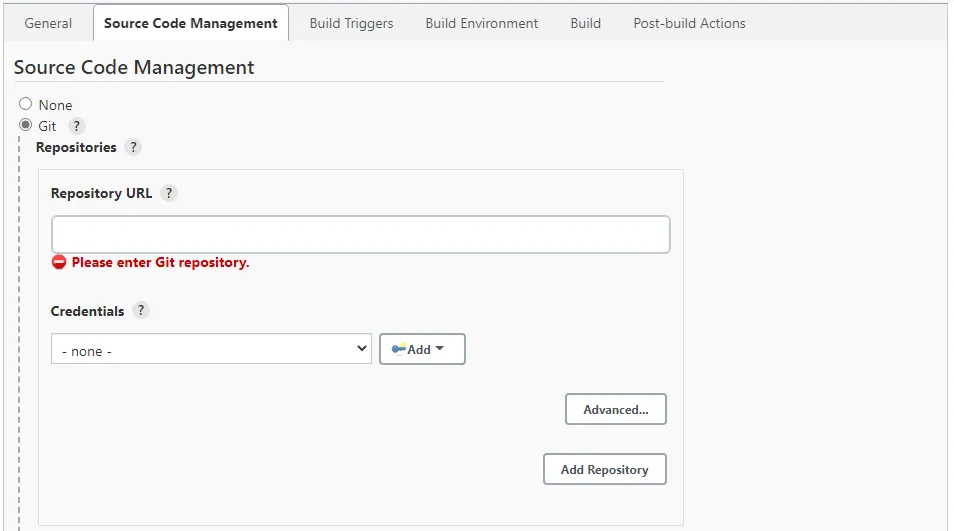
A good example of where you can select global credentials is when creating a pipeline:
- Click New Item in the left menu.
- Enter an item name, select Freestyle project, and click OK.
- Check the Git radio button under the Source Code Management heading. Paste your repo address into the Repository URL field and select your credentials from the Credentials dropdown box.
- Finish setting up your item and click Save.
Jenkinsfiles are text files in your code repo that define what your pipeline does and what it connects to. Jenkinsfiles are part of Jenkins Pipeline - a collection of Jenkins-recommended plugins for Continuous Integration and Continuous Delivery (CI/CD).
This means you can connect to services via your Jenkinsfile from credentials stored in Jenkins.
If you’re using the Blue Ocean plugin, which creates a Jenkinsfile for you when you set up a pipeline, it’s likely you won’t need to engage with Jenkinsfiles at all.
See the Using a Jenkinsfile page on the Jenkins website for more information.
User-tied credentials in Jenkins
Depending on what you connect Jenkins to, or the plugin you use, Jenkins ties some credentials to the logged-in user. Jenkins only stores these credentials when you first connect it with another service. You can’t use these credentials outside of their initial setup and no other user account can access them.
For example, when creating your first pipeline in Blue Ocean (a plugin that simplifies the Jenkins user interface), Jenkins connects to your code repository. If connecting to GitHub, you use a GitHub personal access token (created in your GitHub account’s developer settings) to allow Jenkins to connect to the repo. Jenkins only stores this token for the logged-in user in their own credentials ‘domain’.
In Jenkins, you find these credentials in a different location to global credentials, though the screen for them works in a similar way.
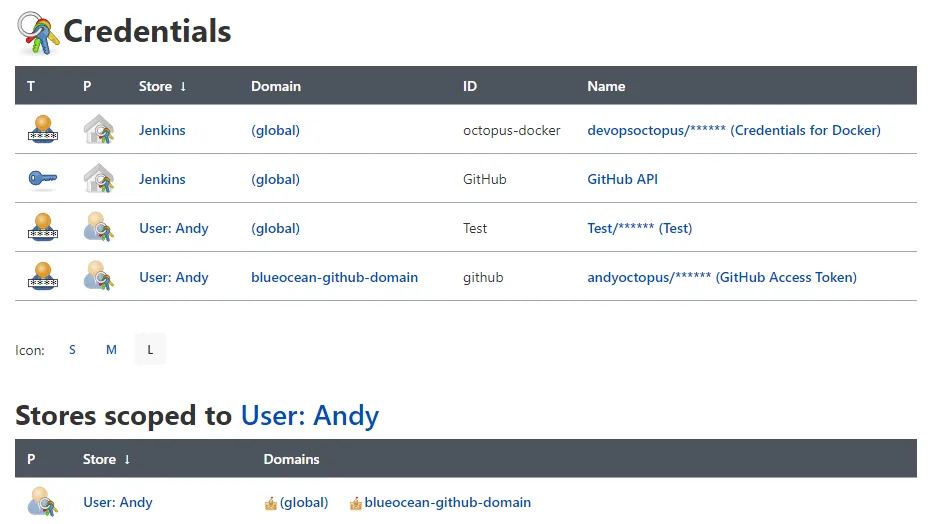
To see your user-tied credentials, click the arrow next to your username in the top-menu and click Credentials.
The top section shows all credentials you have access to, including user and global. When you scroll down, you see headings for all credential stores. In my example, Stores scoped to User: Andy are credentials that only I can use.
What’s next?
See Jenkins’ credentials documentation for more information.
Check out our other posts about configuring Jenkins:
Try our free Jenkins Pipeline Generator tool to create a Pipeline file in Groovy syntax. It’s everything you need to get your Pipeline project started.
Watch our Jenkins Pipeline webinar
We host webinars regularly. See the webinars page for details about upcoming events, and live stream recordings.
Read the rest of our Continuous Integration series.
Happy deployments!
Related posts
The reality of GitOps application recreation
GitOps promises recreatable applications, but 54% of teams say 'partially.' Why confidence dips before soaring and what complete recreation actually requires.

The State of GitOps report: Exploring effective GitOps
Key insights from the first State of GitOps report based on 660 survey responses. Learn how high-performing teams achieve better software delivery, increased reliability, and stronger security through 6 essential GitOps practices.

Inside DevOps with Oluwateniola Olubowale from United Capital
A series where we share lessons learned from those on the frontlines of DevOps. This post features Oluwateniola Olubowale, DevOps Engineer at United Capital.




