I’ve written previously about extending the functionality of Octopus to integrate with HashiCorp Vault and Azure Key Vault using step templates. We’re committed to providing many ways for our customers to succeed with Octopus, so we’re creating more step templates that integrate with other secret managers.
In this post, I walk through a new step template, GCP Secret Manager - Retrieve Secrets. This step template retrieves secrets from Secret Manager on Google Cloud Platform (GCP) for use in your deployments or runbooks.
Getting started
This post assumes some familiarity with custom step templates and the Octopus community library.
In addition, this post doesn’t go into great detail about Secret Manager concepts or how to set up Secret Manager. You can learn more by reading the Secret Manager quickstart guide from Google.
The step template in this post retrieves secrets from Secret Manager using gcloud, the GCP command-line tool. The gcloud tool, version 338.0.0 or higher must be installed on the deployment target or Worker before the step can retrieve secrets successfully.
The step also requires Octopus 2021.2 or newer as it makes use of our recently added built-in support for Google Cloud Platform. The step template has been tested on both Windows and Linux (with PowerShell Core installed).
Authentication
Before you can retrieve secrets from Secret Manager, you must authenticate with Google. In their documentation on creating and accessing secrets, Google describes the role to access secrets:
Accessing a secret version requires the Secret Manager Secret Accessor role (
roles/secretmanager.secretAccessor) on the secret, project, folder, or organization. IAM roles can’t be granted on a secret version.
To learn more about the different roles you can use with Secret Manager, read the access control documentation on how to provide permissions to access sensitive passwords, certificates, and other secrets.
In Octopus, you can authenticate with Google Cloud Platform using the Google Cloud Account we added in version 2021.2
Retrieving secrets
The GCP Secret Manager - Retrieve Secrets step template retrieves one or more secrets from Secret Manager and creates sensitive output variables for each one retrieved.
For each secret, you must provide a version of the secret to retrieve, and optionally provide a custom output variable name.
Always choose a specific secret version Google recommends that for production applications, you should always retrieve secrets with a specific version, and not with the latest version specifier.
Retrieving a single secret requires:
- A Google Cloud account with permission to access the secret, including details of the default project, region, and zone
- The name of the secret to retrieve
An advanced feature of the step template offers support for retrieving multiple secrets at once. This requires entering each secret on a new line.
For each secret retrieved, a sensitive output variable is created for use in subsequent steps. By default, only a count of the number of variables created will be shown in the task log. To see the names of the variables in the task log, change the Print output variable names parameter to True.
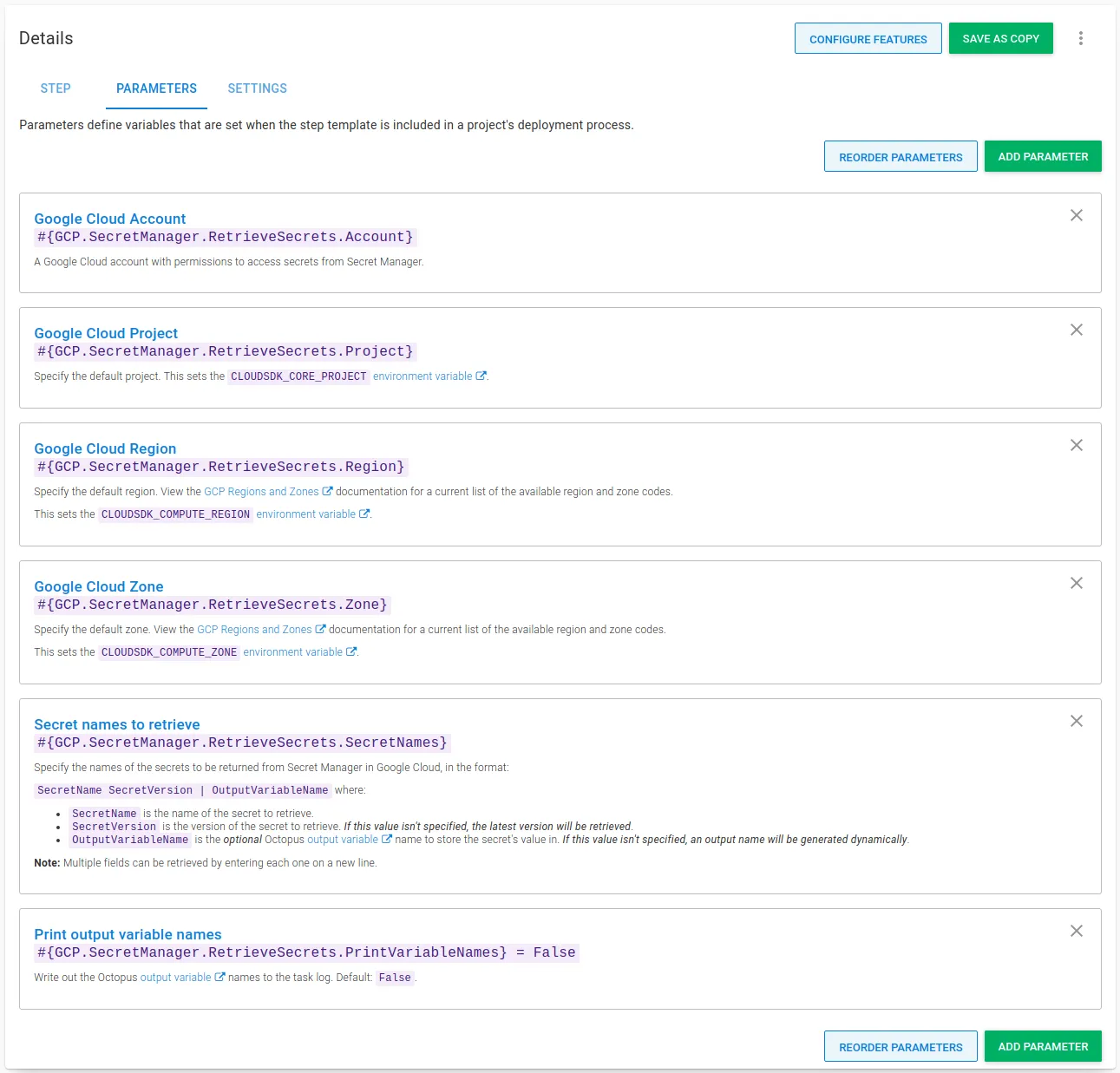
Step template parameters
The step template uses the following parameters:
-
Google Cloud Account: A Google Cloud account with permissions to access secrets from Secret Manager.
-
Google Cloud Project: Specify the default project. This sets the
CLOUDSDK_CORE_PROJECTenvironment variable. -
Google Cloud Region: Specify the default region. This sets the
CLOUDSDK_COMPUTE_REGIONenvironment variable. -
Google Cloud Zone: Specify the default zone. This sets the
CLOUDSDK_COMPUTE_ZONEenvironment variable. -
Secret names to retrieve: Specify the names of the secrets to return from Secret Manager in Google Cloud, in the format:
SecretName SecretVersion | OutputVariableNamewhere:SecretNameis the name of the secret to retrieve.SecretVersionis the version of the secret to retrieve. If this value isn’t specified, the latest version will be retrieved.OutputVariableNameis the optional Octopus output variable name to store the secret’s value in. If this value isn’t specified, an output name will be generated dynamically.
Note: Multiple fields can be retrieved by entering each one on a new line.
-
Print output variable names: Write out the Octopus output variable names to the task log. Default:
False.
Using the step
The GCP Secret Manager - Retrieve Secrets step is added to deployment and runbook processes in the same way as other steps.
After you add the step to your process, fill out the parameters in the step:
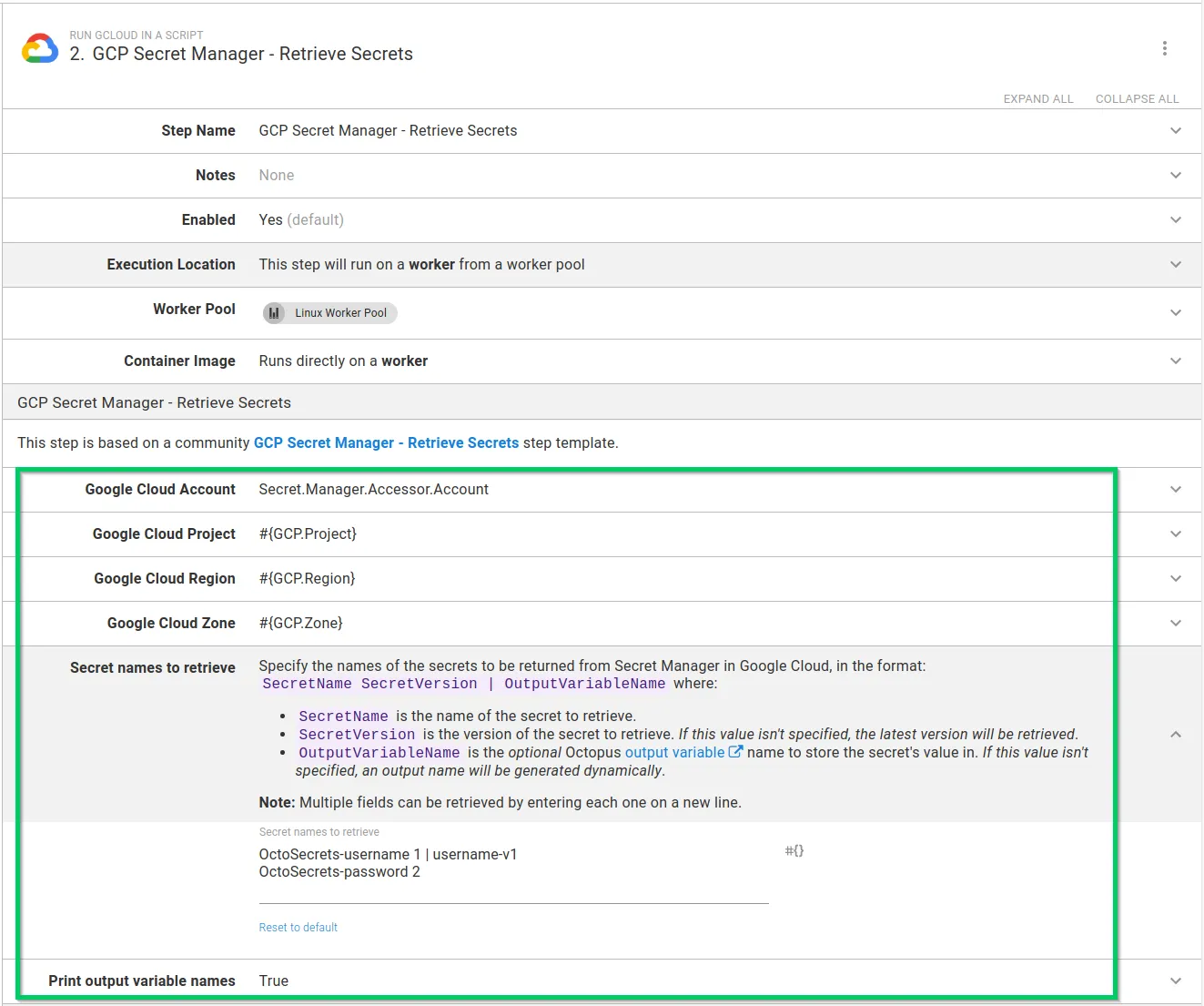
After you fill in the parameters, you can execute the step in a runbook or deployment process. On successful execution, any matching secrets will be stored as sensitive output variables. If you configured your step to print the variable names, they appear in the task log:
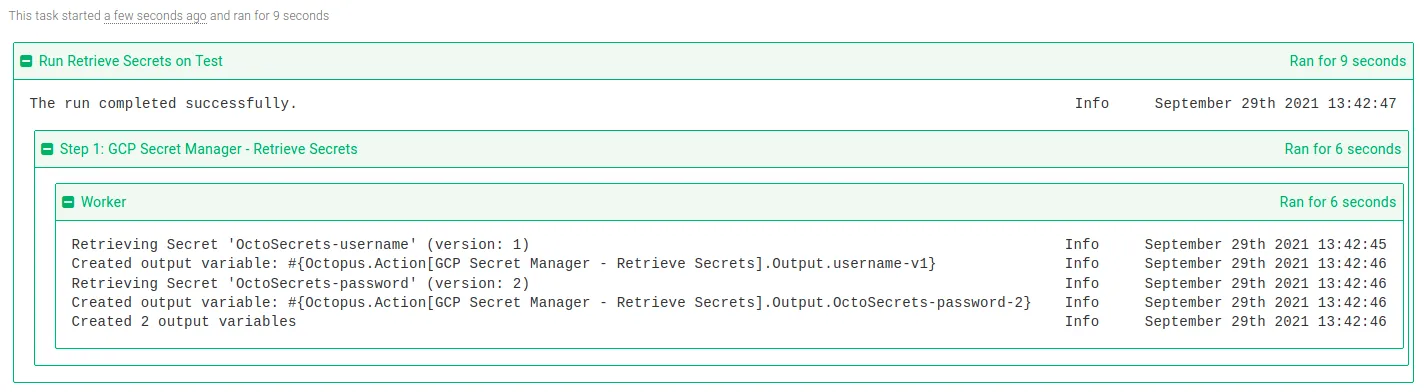
In subsequent steps, output variables created from matching secrets can be used in your deployment or runbook.
Tip: Remember to replace GCP Secret Manager - Retrieve Secrets with the name of your step for any output variable names.
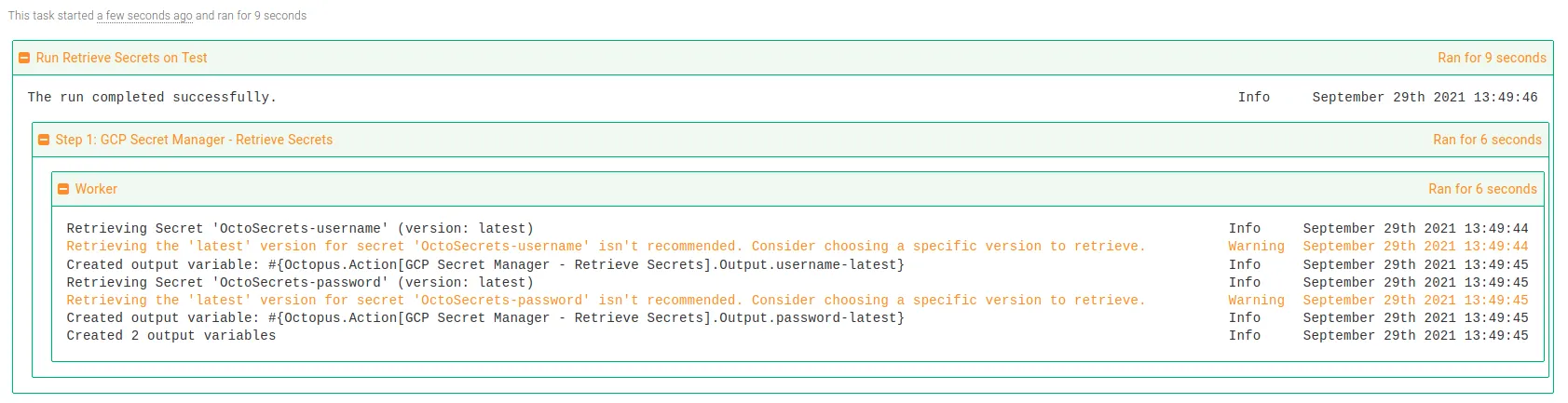
Although not recommended, it’s possible to retrieve the latest version of a secret. You can omit the version from the secret names parameter like this:
OctoSecrets-username | username-latestAlternatively, you can use the latest version specifier like this:
OctoSecrets-password latest | password-latestIn both cases, the step template will send a warning to the task log:
Conclusion
The GCP Secret Manager - Retrieve Secrets step template demonstrates that it’s easy to integrate with Google Cloud Secret Manager and make use of secrets stored there with your Octopus deployments or runbooks.
Happy deployments!
Related posts

Deploying LLMs with Octopus
LLMs are now a common component of modern applications, but deploying them with Kubernetes requires careful consideration. This article explores the challenges and best practices for deploying LLMs in a Kubernetes environment.
The reality of GitOps application recreation
GitOps promises recreatable applications, but 54% of teams say 'partially.' Why confidence dips before soaring and what complete recreation actually requires.

The State of GitOps report: Exploring effective GitOps
Key insights from the first State of GitOps report based on 660 survey responses. Learn how high-performing teams achieve better software delivery, increased reliability, and stronger security through 6 essential GitOps practices.




