When you’re working with any cloud provider, you want an easy way to connect to the cloud. You don’t want to worry about creating custom scripts, API calls, and duct-tape workarounds just to deploy code or build infrastructure with Continuous Delivery.
Octopus Deploy has a clean and straight-forward way to connect to many cloud providers. In this blog post, you will learn how to connect Octopus Deploy to AWS.
Prerequisites
To follow along with this blog post, you need to have:
- An AWS account.
- An Octopus Deploy server, either an on-premises instance of Octopus Server or an Octopus Cloud instance.
You can get started with either Octopus Server or Octopus Cloud for free.
Creating an IAM user
Before deploying from Octopus Deploy to AWS, you need an authentication method. Because Octopus Deploy will deploy infrastructure or applications to AWS, AWS needs to know who Octopus Deploy is. The typical authentication method for AWS is Identity and Access Management (IAM), which provides an access key and secret.
Create the IAM user in the UI
- To create an IAM user in the AWS UI, open a web browser and go the AWS console:
- Under Find Services in the search bar, type in IAM.
- Click on the Users option under Access management.
- To create the new user that will have access to AWS from Octopus Deploy, click the blue Add user button.
- Under Set user details, create an appropriate name for the user name. For example,
OctopusDeployAccount. - In the Select AWS access type section, select the Programmatic access option. Octopus Deploy will make API calls to AWS at the SDK level.
- Click the blue Next: Permissions button.
Permissions for the user are going to depend on what AWS services you want Octopus Deploy to have permissions for. For example, let’s say you want Octopus Deploy to just deploy EC2 instances, in that case, you give the IAM user access to something like AmazonEC2FullAccess.
-
For the purposes of this blog post, we want Octopus to communicate with all AWS services, so we’ll choose the
AdministratorAccesspolicy under Attach existing policies directly. After you choose theAdministratorAccessoption, click the blue Next: Tags button as shown in the screenshot below. -
Tags aren’t necessary for the purposes of this blog post, so you can click the blue Next: Review button.
-
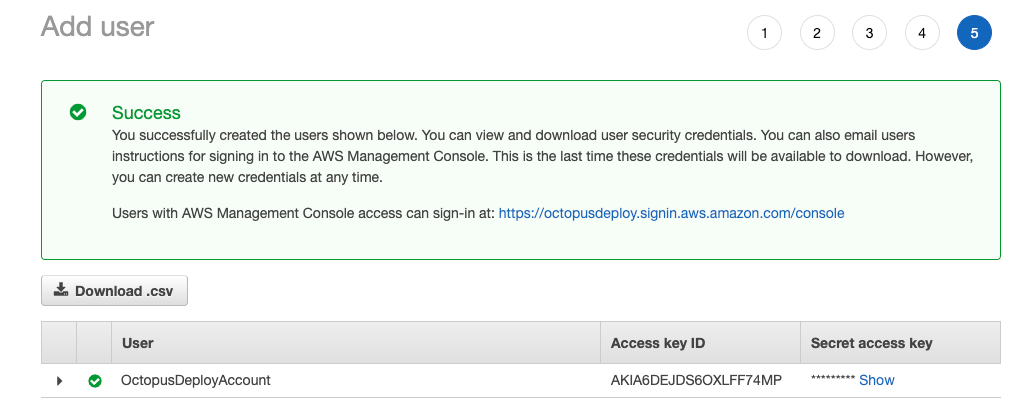
Finally, to create the new IAM user, click the blue Create user button.
You will be shown a screen that contains the Access key ID and the Secret access key. Save the Secret access key in a secure location because you will not be able to access it again. However, you can create a new secret access key if you lose this one. The Access key ID and Secret access key will be used for the Octopus Deploy authentication.
IAM user on the CLI
As you saw in the previous section, creating an IAM user and adding them to the appropriate policy can be a bit cumbersome and requires a lot of clicking around. If you use the AWS CLI, there is a much easier way with just a few lines of code.
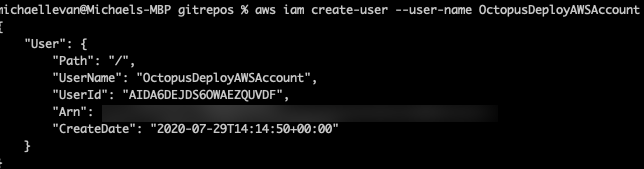
The first piece of code creates the new IAM user:
aws iam create-user --user-name OctopusDeployAWSAccountThe output should be similar to the screenshot below:
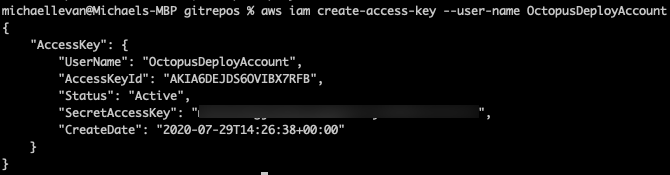
Next, you need to create the Secret access key. The Secret access key acts as a password of sorts.
To create the Secret access key, run the code below:
aws iam create-access-key --user-name OctopusDeployAccountThe output should look similar to the screenshot below:
You are now ready to connect the AWS IAM account to Octopus Deploy.
Connecting AWS to Octopus Deploy
In the previous section you learned about creating the ability to have Octopus Deploy interact with AWS at a programmatic level. Now that you understand the purpose of the access and secret keys, it’s time to set up the AWS account in Octopus Deploy.
- Open up a web browser and go to the Octopus Deploy Web Portal:
- Navigate to {{Infrastructure, Accounts}} to set up the new AWS account.
- Under Accounts, click the green ADD ACCOUNT button and choose AWS Account:
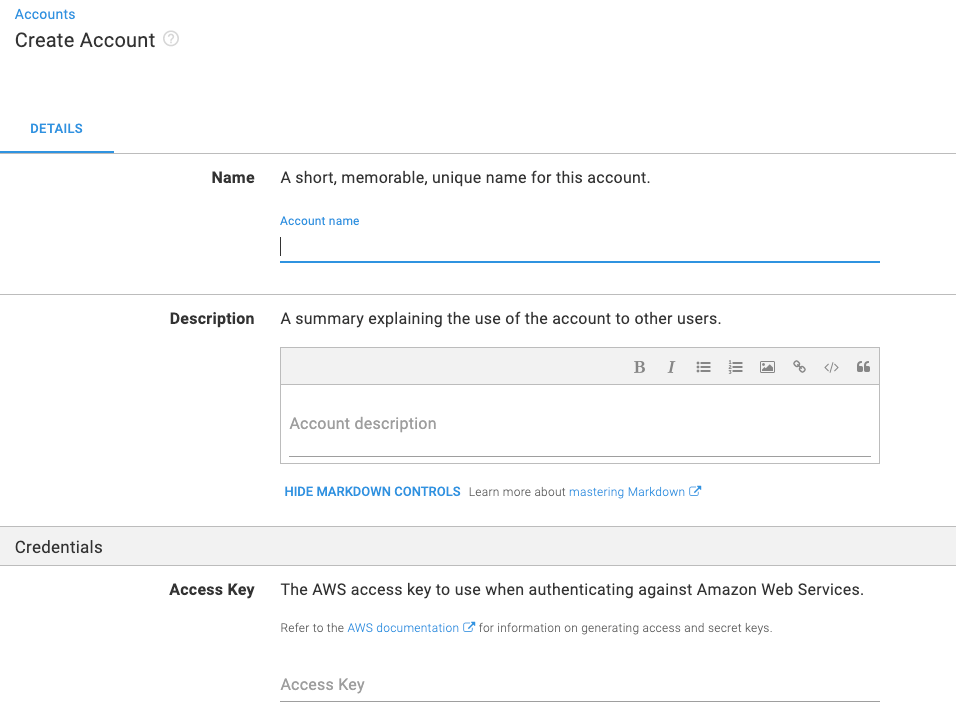
- Under Details, you can add metadata about your account; the name and description.
- Next, under Credentials, you can add the AWS access key and secret key.
- Finally, you can set restrictions under the Restrictions section. For example, I’ve chosen to allow this account for my Dev environment only.
- Click the green SAVE button on the top of the page.
Congrats! You have successfully set up an AWS account in Octopus Deploy.
Conclusion
The need to interact with different cloud-based platforms is not a need that will go away. Regardless of what Continuous Delivery and Deployment tool you’re using, there will always be a reason for authentication from the CD tool to a cloud, or even on-premises, platform.
Happy Deployments!





