Your security team wants private connectivity between tools you use, but your organization loves the convenience of cloud-hosted applications that help the business run. Octopus Cloud with Azure Private Endpoints gives you both.
This functionality allows your teams and tools to access Octopus Deploy over Azure private network connections that bypass the public internet, reducing your attack surface, keeping your network traffic within your boundaries, without sacrificing any of the convenience and operational benefits our fully managed cloud offering provides.
The case for private connectivity
Accessing cloud-hosted tools usually requires a trade-off: choose between the convenience of managed SaaS platforms and the security of private networking. Accessing SaaS platforms over the public internet is a valid approach for many customers. It meets their security and risk tolerance requirements and a standard way of operating. Octopus Cloud is secure and compliant out of the box with internationally recognized security standards.
However, it can become particularly challenging when operating in regulated industries like financial services, healthcare, or government, where strict requirements look to prevent traffic from traversing public networks, especially for tools that touch production systems. That convenient SaaS deployment tool doesn’t look so convenient for these organizations anymore.
Some organizations prefer private connectivity by default as part of their broader security strategy. While zero-trust principles can certainly work with public internet connections through well-implemented authentication and encryption, many teams find that private network paths provide an additional layer of defense and better align with their risk management approach.
Companies with significant on-premises infrastructure encounter additional complexity. Secure connectivity between private networks and cloud services is needed, but traditional solutions often involve complex VPN setups that create operational overhead and potential failure points.
Beyond compliance, many teams value controlling their critical traffic routes. When deploying software that runs your business, you want private infrastructure, predictable network paths, and a reduced attack surface to provide that extra assurance.
For Octopus Deploy, these factors typically mean customers choose to deploy and manage Octopus Server on their infrastructure, secured by their private network. While this is a valid approach, for customers who don’t want the overhead of managing and running Octopus Server, we’ve introduced functionality for you to attach an Azure Private Endpoint to your Octopus Cloud instance, providing a path to route traffic to your Octopus Cloud instance over your private network infrastructure.
Inbound access to Octopus Cloud
Using Microsoft’s Private Link Service, the primary use case involves creating a private endpoint in your Azure virtual network that connects directly to your Octopus Cloud instance. This connection creates a secure tunnel that allows your teams and applications to interact with Octopus Deploy without touching the public internet.
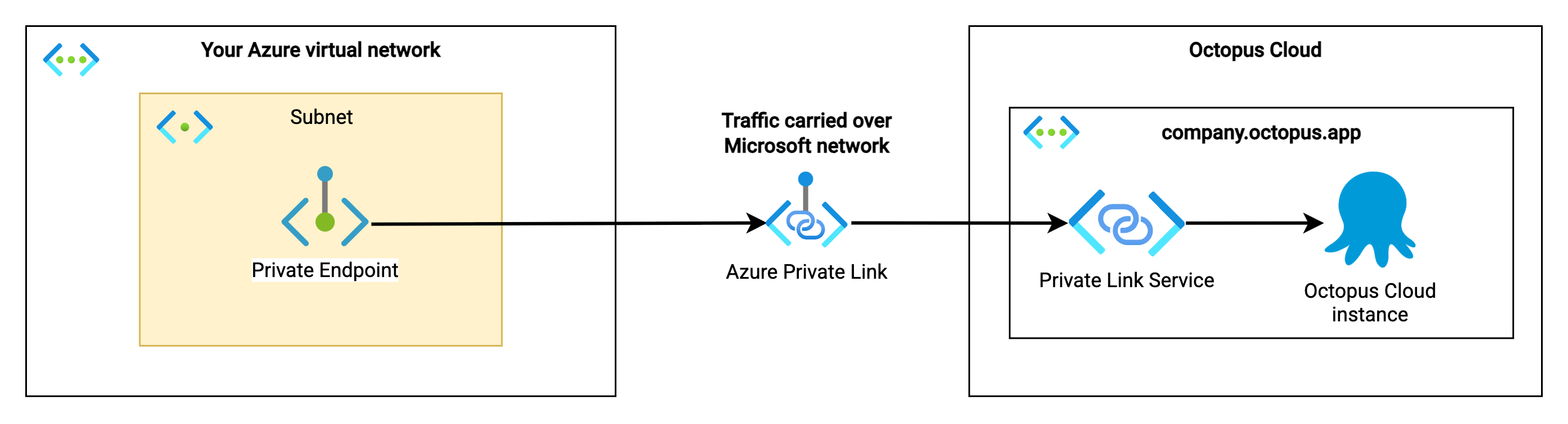
- Your Azure subscription hosts a private endpoint in your chosen virtual network and subnet
- This private endpoint connects directly to Octopus Deploy’s private link service for your Octopus Cloud instance
- All communication between your environment and Octopus Cloud travels over Azure’s private backbone. This includes communication from private networks connected to your Azure network infrastructure, like other public clouds, or on-premises networks for hybrid network setups.
Outbound access from Octopus Cloud
We’re also exploring secure outbound connectivity from your Octopus Cloud instance to resources in your private network infrastructure.
The diagram below illustrates this scenario using Sonatype Nexus Repository as an example, but you can substitute any service that Octopus Deploy needs to access. This could be a package repository, configuration management system, or any other tool that resides in your Azure virtual network, or connects through your Azure network to other private infrastructure in different clouds or on-premises environments.
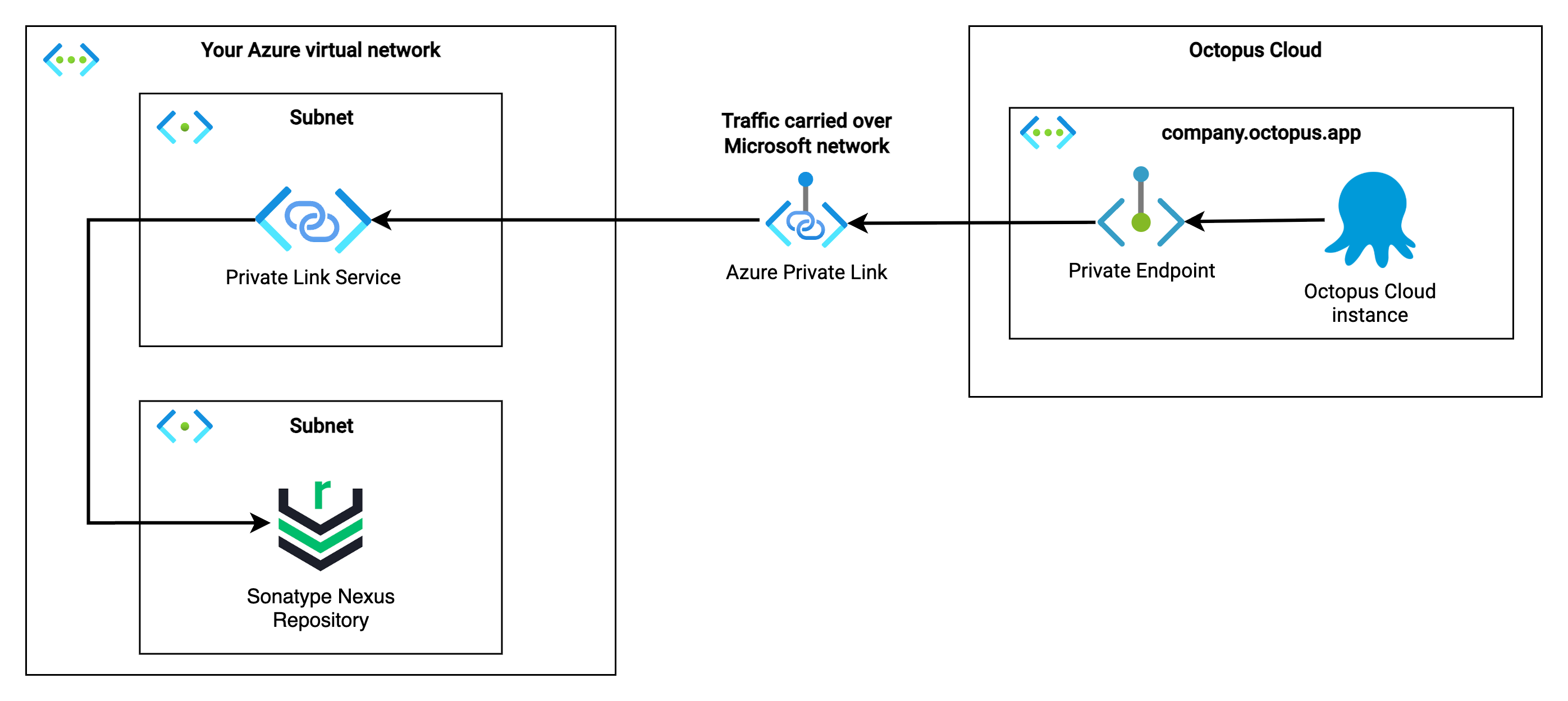
This configuration unlocks many different scenarios, with one example being:
- Your development team pushes code to your private repositories
- Your CI system builds artifacts and stores them in your privately accessible package manager (like Sonatype Nexus, JFrog Artifactory, or others)
- When running a release, Octopus Deploy securely fetches artifacts from your private services using outbound private network connectivity
- All traffic between Octopus Cloud and your private resources stays within Azure’s backbone or your connected private networks
Interested to learn more?
Whether you need private connectivity for compliance reasons or as part of your broader security strategy, Azure Private Endpoints for Octopus Cloud deliver enterprise-grade security without sacrificing functionality or the operational advantages of Octopus Cloud.
This functionality brings private networking to our cloud-hosted platform, available to Octopus Cloud Enterprise tier customers. Professional tier customers with private connectivity needs should also reach out - we’re always interested in understanding your requirements.
Happy Deployments!