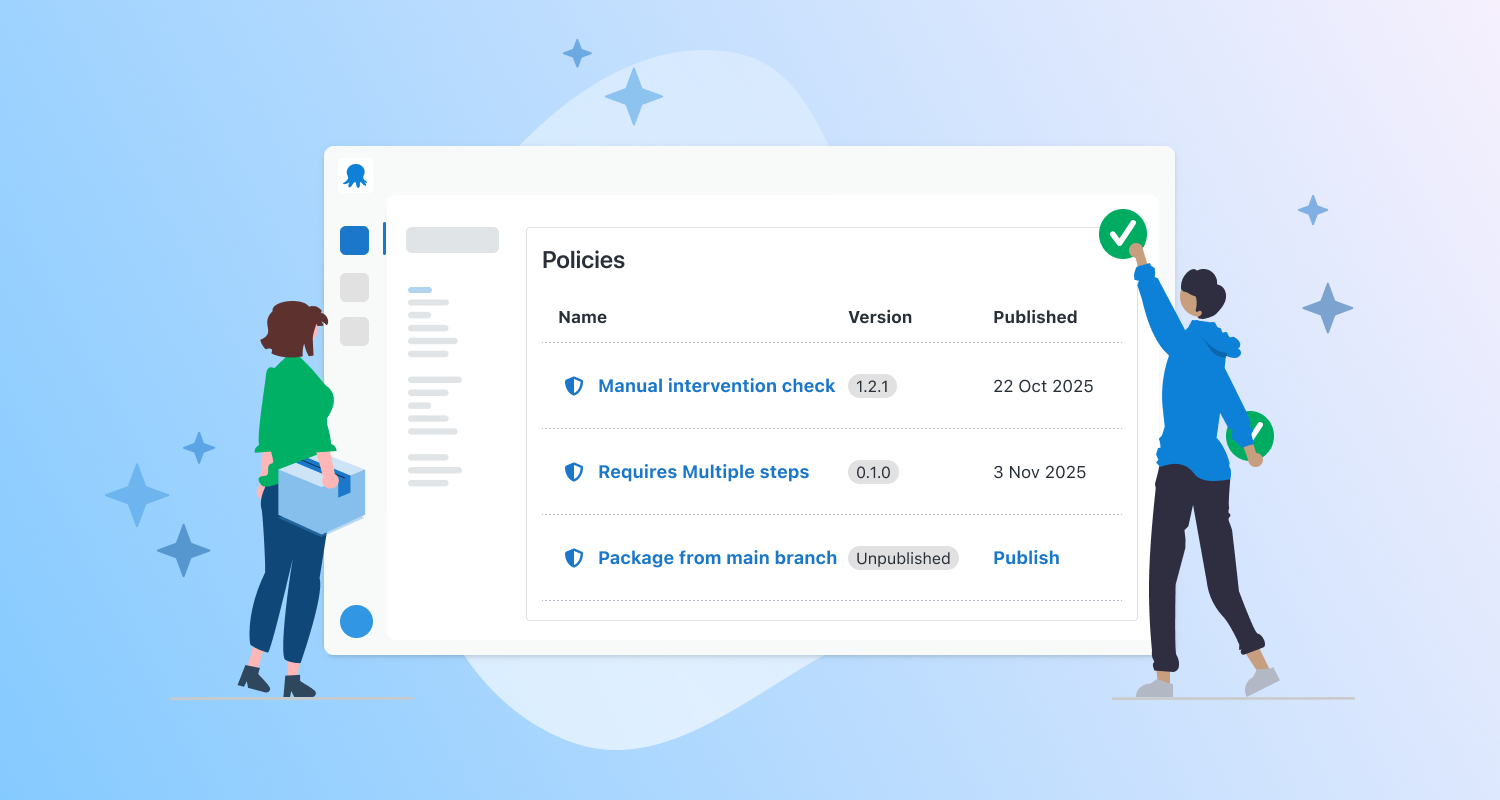
Today we are excited to announce the launch of Policies to all Enterprise customers. Policies enable users to easily enforce deployment standards across their Octopus instance without manual effort.
What are Policies?
Policies in Octopus are designed to ensure compliance and governance by default, making it easier to enforce deployment controls at scale. This approach allows you to shift compliance left, alleviating the burden of manual audits and enabling you to maintain high standards across your organization. With policies, you can enforce organization-wide compliance across teams and regions, moving governance out of Confluence docs and Slack threads and into the heart of your delivery pipeline.
Using Rego, you can write custom policy checks that align with your requirements, block non-compliant deployments, and access detailed audit logs of policy evaluation events. This method ensures compliance is not an afterthought; it is embedded within every deployment pipeline, providing a seamless and efficient way to uphold governance standards across all activities.
Why use Policies?
Policies streamline the enforcement of standards across all deployments by automating compliance checks and governance measures.
Consider implementing policies if:
- You want to ensure that every deployment conforms to predefined standards without manual effort.
- You wish to manage these standards centrally, allowing for consistent application across your organization and easy updating of standards.
While policies may not be necessary in every deployment scenario, they are invaluable if maintaining compliance and security is a priority. By embedding policies into your deployments, you can minimize risks and ensure that all teams are aligned with your organizational standards.
What policies can I enforce?
Check that a deployment step is present when deploying to production This policy can check that any step (Octopus step, Custom step template, Community Step template, or Process Template) exists in a deployment process (or runbook process), and:
- Is not skipped
- Is enabled
- Is at a certain position in the deployment process (or runbook process)
- Is a certain version (for custom step templates, community step templates, and process templates)
- Isn’t run in parallel with another step.
when deploying to any environment.
Example: I can check that all deployments to production must have my “Security-Scan” process template present at the end of every deployment and is of version 2.0.0.
Check that a package, container image, or deployment process from a version-controlled deployment process is from the main / master branch when deploying to production.
This policy can check that a:
- Package
- Container Image
- Deployment process from a version-controlled process
are from the main / master branch when deploying to any environment.
Example:
I want to ensure that all deployment processes in my version controlled project are from the main / master branch so that only approved deployment processes are being used to deploy to production.
To get started, please visit our documentation, which contains examples of common scenarios that you can use as a reference.
Conclusion
Policies are now available to all Enterprise customers. If you are on Enterprise Cloud, you can click the Platform Hub icon to get started. If you are using a self-hosted version of Octopus, please upgrade to the 2025.4 server release to adopt Policies.
Happy deployments!