-

Creating Kubernetes pods, ReplicaSets, and deployments
-

Creating Kubernetes services
-

Deploying to Kubernetes with Octopus
-

Multi-environment deployments
-

Installing a dashboard
-

Observing deployment strategies
-
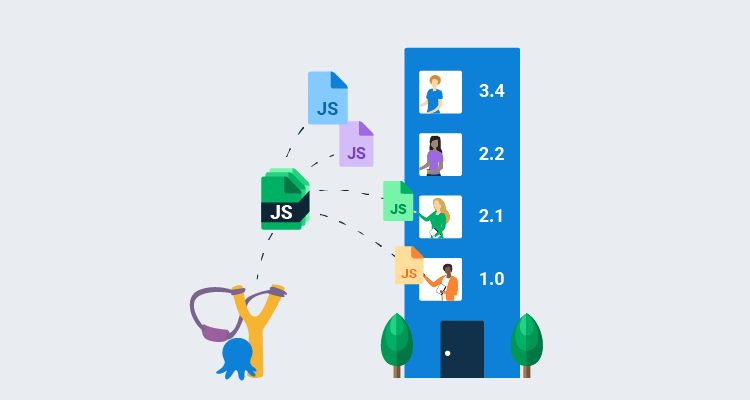
Managing all consumers of your JavaScript library as tenants
-

Our most popular webinars in 2021
-
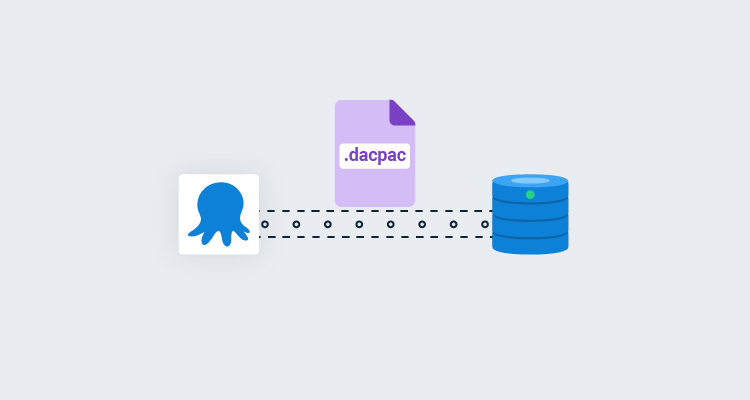
Deploy SQL Server DACPAC with Octopus Deploy
-

Octopus Deploy's response to Log4j
-

Deploying database changes to Cassandra
-

Safe schema updates - Strangling the monolith










