-
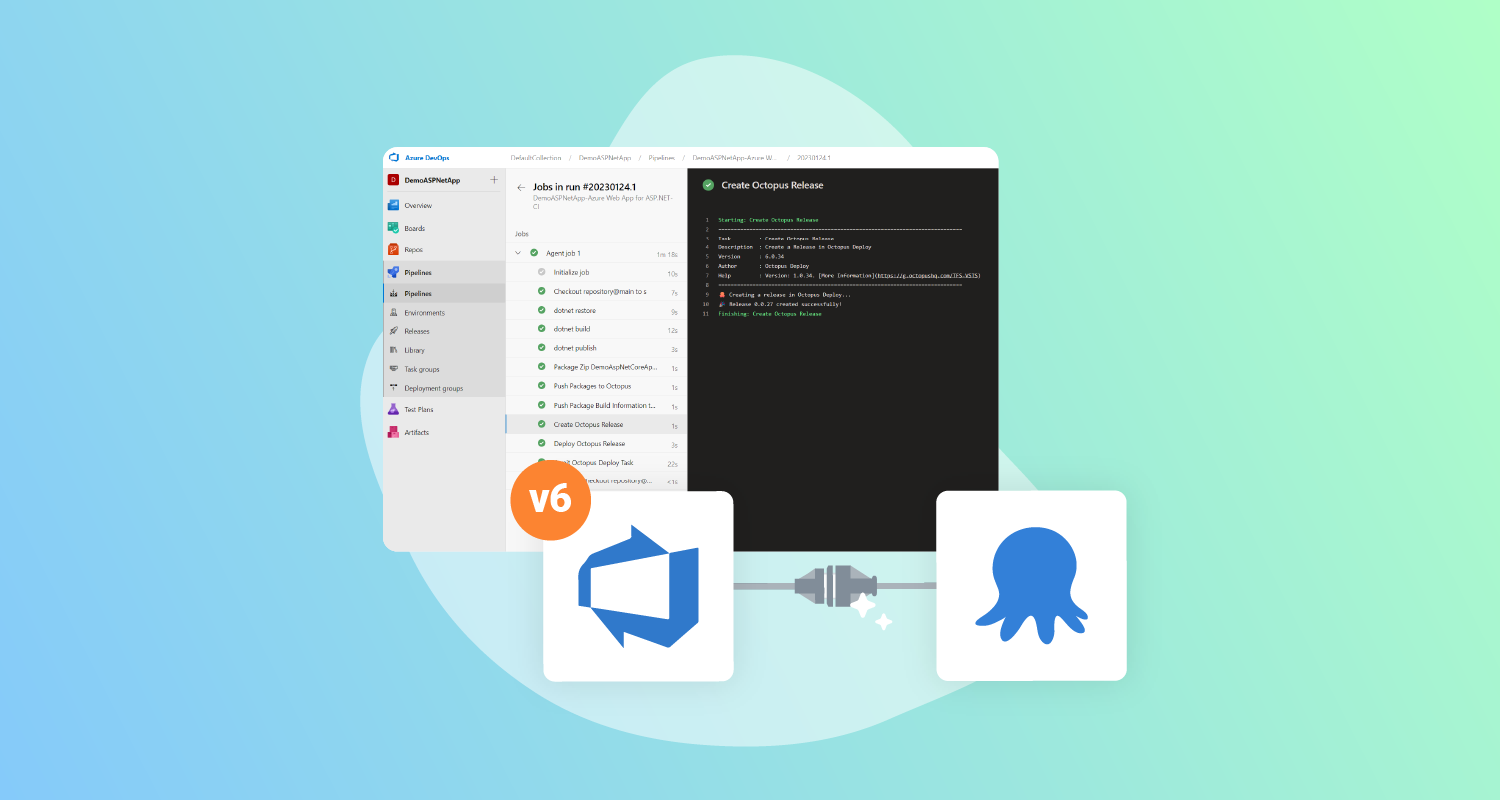
New in Azure DevOps for Octopus Deploy v6
-

Outage on octopus.com - report and learnings
-

Octopus Cloud connectivity disruption - report and learnings
-
An introduction to build servers and Continuous Integration
-

The key assumption of modern work culture
-

The new DevOps performance clusters
-

DevOps and Platform Engineering
-

Validating Config as Code projects
-

Synchronizing projects in managed spaces
-

Exploring the managed instance and space patterns
-

Enterprise deployment patterns reference implementation
-

Octopus enterprise deployment patterns









