-
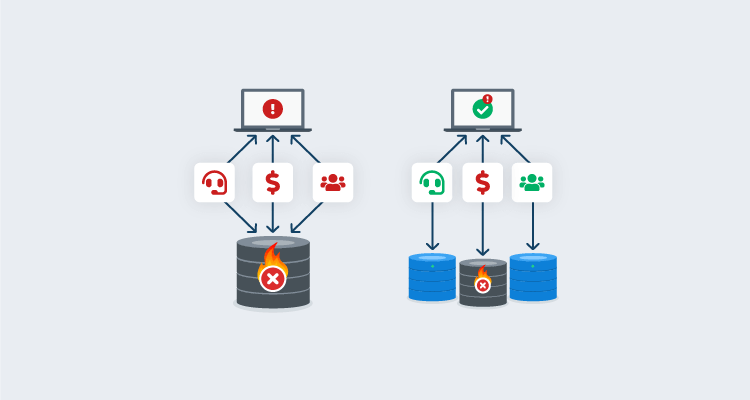
Safe schema updates - Loose coupling mitigates tech problems
-
Introducing the Workato connector for Octopus Deploy
-
Introducing Google Cloud Platform integration for Octopus Deploy
-
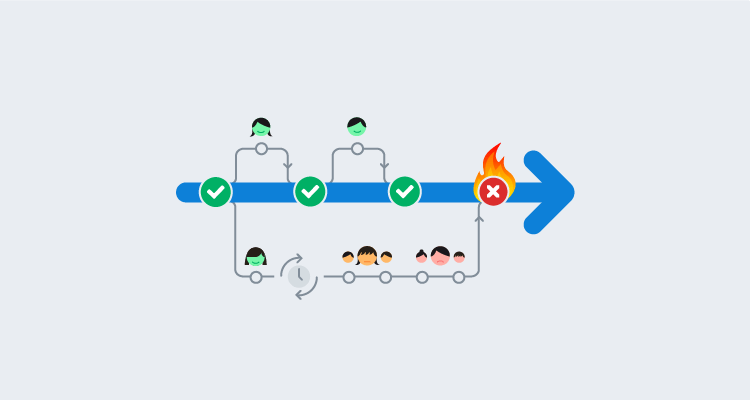
Safe schema updates - Continuous Integration is misunderstood
-

Octopus 2021 Q3: Google Cloud support with centralized Kubernetes deployments and runbooks
-

Safe schema updates - Resilient vs robust IT systems
-

Chaos engineering and runbooks
-

Safe schema updates - Database delivery hell
-

DevOps, runbooks, and kubectl
-

Why use Octopus for Kubernetes deployments?
-
Migrating 426 Nancy API endpoints to ASP.NET Core controllers
-

Supporting Octopus Deploy customers










