-

At the helm with Jessica Ross
-
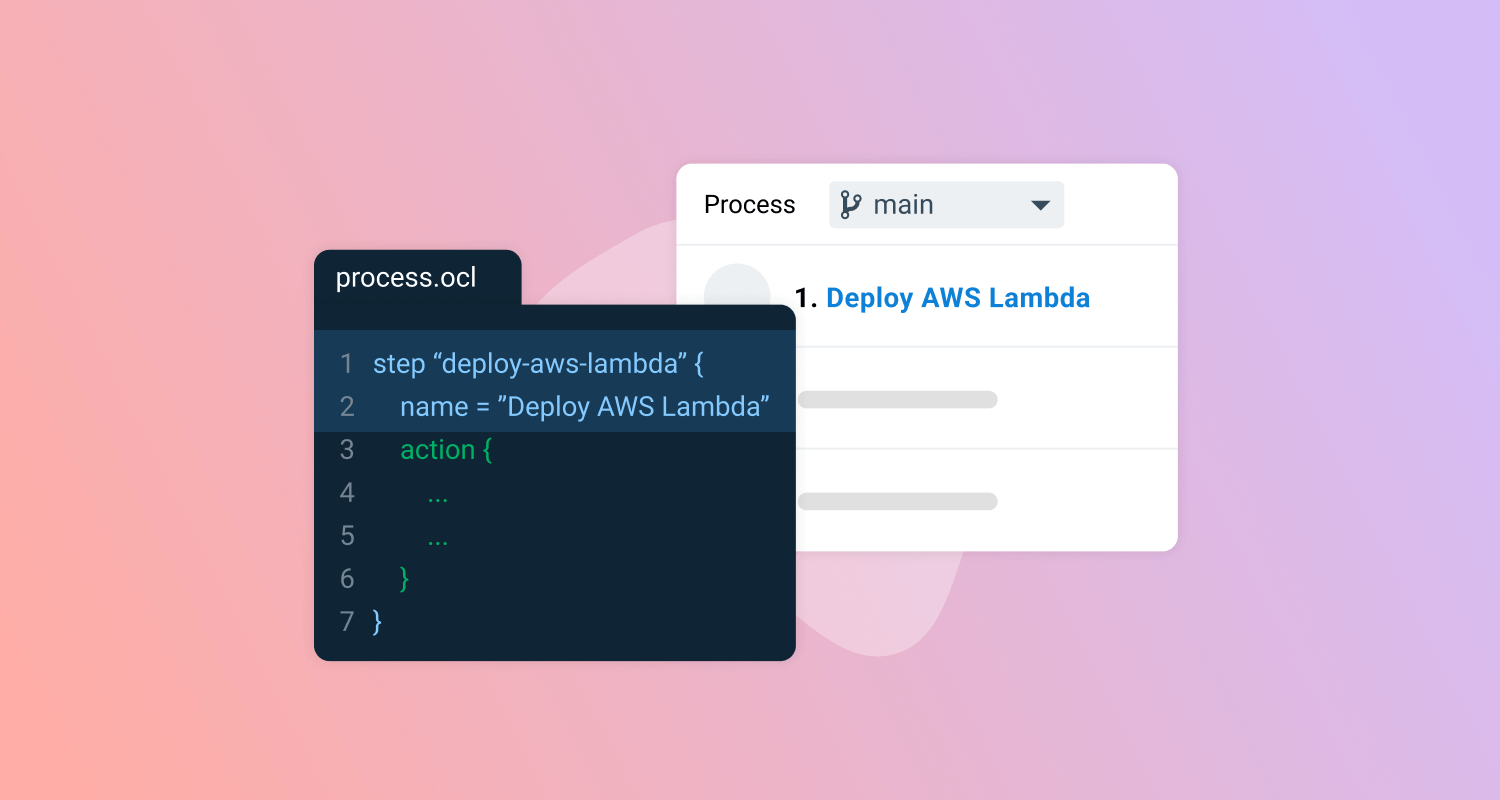
Introducing slugs in Config as Code
-

Request for Comments - Migrating from scriptcs to dotnet-script
-
Using GitLab feeds with Octopus Deploy
-

Containers - what you need to get started
-

The benefits of containerization
-

Microservices and frameworks
-

Using the new ECS deployment step
-
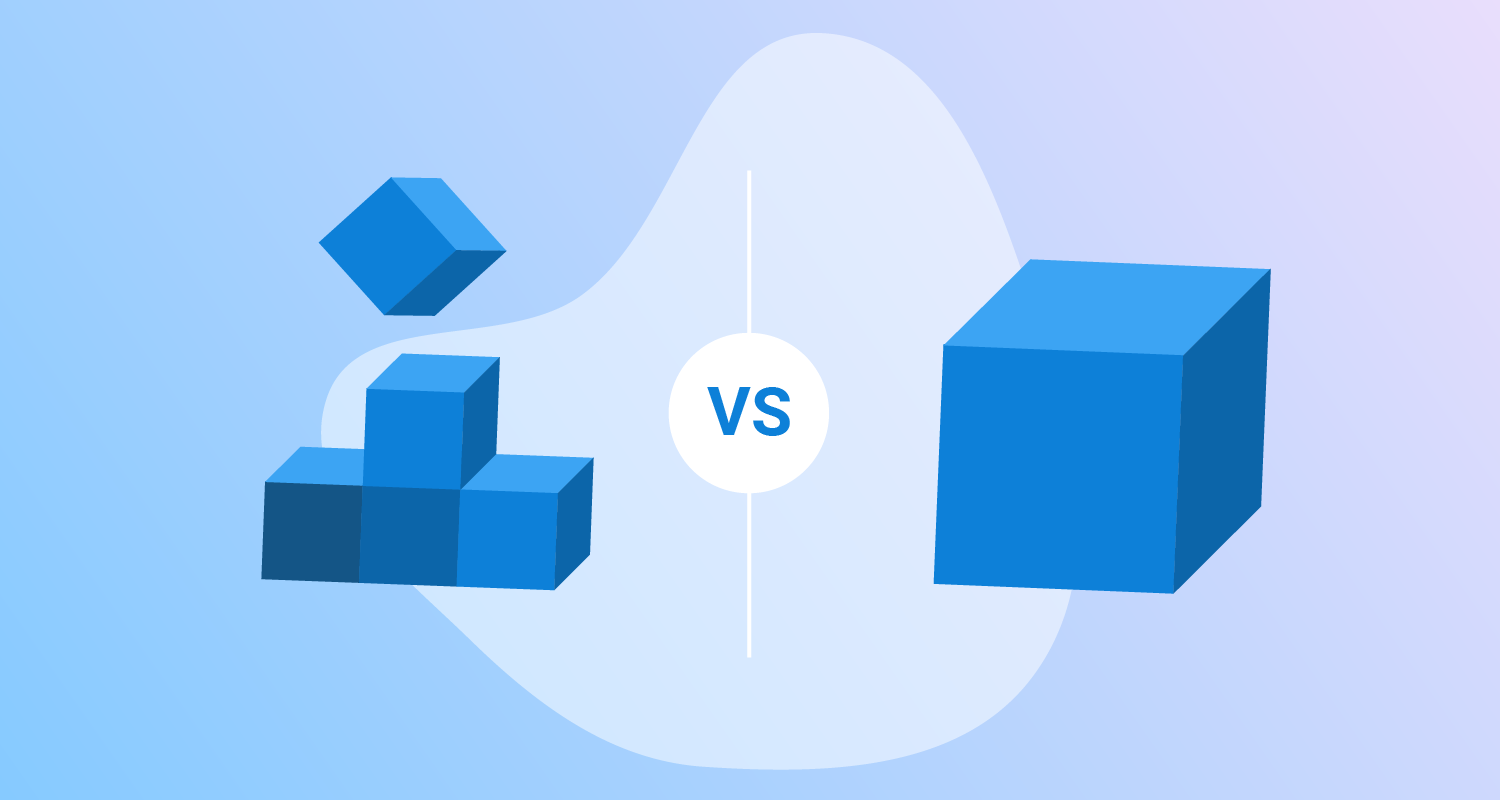
Monoliths versus microservices
-

Runbook lessons learned and recommendations
-

Source control your Azure Bicep files
-

Azure Bicep and Octopus Deploy













