Communication settings
To verify the communication settings, On the Tentacle machine, open the Tentacle Manager application from the Start screen or Start menu.
- Ensure that the Tentacle is in listening mode. Below the thumbprint, you should see the text This Tentacles listens for connections on port 10933.
- Check the port that the Tentacle listens on.
- Check that the Octopus Server thumbprint shown in light gray in the Tentacle manager matches the one shown in the Configuration ➜ Thumbprints screen in the Octopus Web Portal.
Note, that there are two thumbprints displayed - that of the Tentacle itself (shown first in bold) and the thumbprints of trusted servers (shown inline in the gray text).
If any of the communications settings are incorrect, choose Delete this Tentacle instance…. After doing so, you’ll be presented with the Tentacle installation wizard, where the correct settings can be chosen. If the settings are correct, continue to next step.
Check the connections
To help with diagnostics, we’ve included a welcome page you can connect to from your web browser.
When you conduct these checks:
- If you’re presented with a prompt to “confirm a certificate” or “select a certificate” choose “Cancel” - don’t provide one.
- If you’re presented with a warning about the invalidity of the site’s certificate, “continue to the site” or “add an exception” (Octopus Server uses a self-signed certificate by default).
On the Tentacle machine, open a web browser and navigate to https://localhost:10933 (or your chosen Tentacle communications port if it isn’t the default). Make sure you use an HTTPS URL is used.
The page shown should look like the one below.
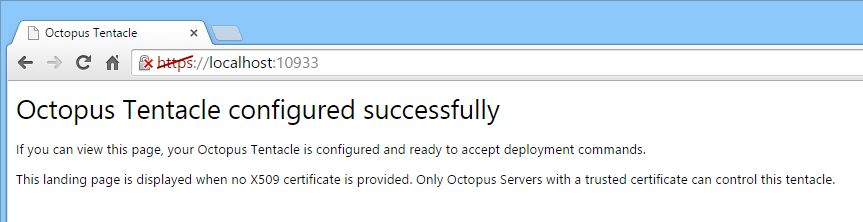
If you can’t browse to the page…
If this is where your journey ends, there’s a problem on the Tentacle machine. It is very likely that the Tentacle is unable to open the communications port, either because of permissions, or because another process is listening on that port. Using the Windows netstat -o -n -a -b command can help to get to the bottom of this quickly. If you’re still in trouble, check the Tentacle log files and contact Octopus Deploy support.
Next, repeat the process of connecting to the Tentacle with a web browser, but do this from the Octopus Server machine.
When forming the URL to check:
- First try using the Tentacle’s DNS hostname, e.g.
https://my-tentacle:10933. - If this fails, try using the Tentacle’s IP address instead, e.g.
https://1.2.3.4:10933- success using the IP address but not the DNS hostname will indicate a DNS issue.
If you can’t connect… Failing to connect at this step means that you have a network issue preventing traffic between the Octopus Server and Tentacles. Check that the Tentacle port is open in any firewalls, and that other services on the network are working. There’s not usually much that Octopus Deploy Support can suggest for these issues as networks are complex and highly varied. Having the network administrator from your organization help diagnose the issue is the best first step. If that draws a blank, please get in touch.
Remember to check both the built-in Windows Firewall, and any other firewalls (in Amazon EC2, check your security group settings for example).
Watch out for proxy servers or SSL offloading… Octopus and Tentacle use TCP to communicate, with special handling to enable web browsers to connect for diagnostic purposes. Full HTTP is not supported, so network services like SSL offloading are not supported, and proxies are not supported in earlier versions of Octopus Deploy. Make sure there’s a direct connection between the Octopus Server and Tentacle, without an HTTP proxy or a network appliance performing SSL offloading in between.
Also see, advanced support for HTTP proxies.
Tentacle ping
We have built a small utility for testing the communications protocol between two servers called Tentacle Ping. This tool helps isolate the source of communication problems without needing a full Octopus configuration. It is built as a simple client and server component that emulates the communications protocol used by Octopus Server and Tentacle.
In Octopus 3.0 you will need TentaclePing and TentaclePong, you cannot test directly to Octopus Server nor Tentacle:
- Run TentaclePing on your Octopus Server machine (which is the client in this relationship).
- Run TentaclePong on your Tentacle machine (which is the server in this relationship).
Use the output to help diagnose what is going wrong.
Check the IP address
Your Octopus Server or Tentacle Server may have multiple IP addresses that they listen on. For example, in Amazon EC2 machines in a VPN might have both an internal IP address and an external addresses using NAT. Octopus Server and Tentacle Server may not listen on all addresses; you can check which addresses are configured on the server by running ipconfig /all from the command line and looking for the IPv4 addresses.
Schannel and TLS configuration mismatches
Octopus uses Schannel for secure communications and will attempt to use the best available protocol available to both servers. If you are seeing error messages like below, try Troubleshooting Schannel and TLS:
Client-side:System.Security.Authentication.AuthenticationException: A call to SSPI failed, see inner exception. ---> System.ComponentModel.Win32Exception: One or more of the parameters passed to the function was invalid
Server-side:System.IO.IOException: Unable to read data from the transport connection: An existing connection was forcibly closed by the remote host.
Other error messages
Halibut.Transport.Protocol.ConnectionInitializationFailedException: Unable to process remote identity; unknown identity ‘HTTP/1.0’
If a Tentacle health-check fails with an error message containing this error message, then there is network infrastructure inserting a web page into the communication. The most common components to do this are firewalls and proxy servers so it’s recommend to check your network setup to verify connectivity between the two servers using the information above and then update your infrastructure appropriately.
Halibut.HalibutClientException: An error occurred when sending a request to ‘https://my-tentacle:10933’, before the request could begin: Attempted to read past the end of the stream.
If your Octopus server certificate was generated with SHA1 then you might get this error when connecting to modern Linux distributions, as the default security configuration now rejects communication using SHA1. To regenerate your Octopus server certificate, follow the documentation How to regenerate certificates with Octopus Server and Tentacle.
Check for zombie child processes locking TCP ports
If Tentacle fails to start with an error message like this: A required communications port is already in use.
The most common scenario is when you already have an instance of Tentacle (or something else) listening on the same TCP port. However, we have seen cases where there is no running Tentacle in the list of processes. In this very specific case it could be due to a zombie PowerShell.exe or Calamari.exe process that was launched by Tentacle that is still holding the TCP port. This can happen when attempting to cancel a task that has hung inside of Calamari/PowerShell. Simply rebooting the machine, or killing the zombie process will fix this issue, and you should be able to start Tentacle successfully.
Check the server service account permissions
If the Tentacle is running as the Local System account you can skip this section.
If the Tentacle is running as a specific user, make sure that the user has “full control” permission to the Octopus Home folder on the Tentacle machine. This is usually C:\Octopus - apply permissions recursively.
Check the load time
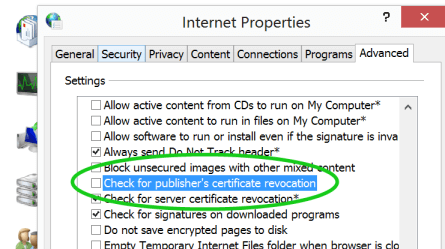
In some DMZ-style environments without Internet access, failing to disable Windows code signing certificate revocation list checking will cause Windows to pause during loading of the Octopus applications and installers. This can have a significant negative performance impact, which may prevent Octopus and Tentacles connecting.
To test this on a listening Tentacle, run:
Tentacle.exe helpIf the command help is not displayed immediately (< 1s) you may need to consider disabling the CRL check while the Tentacle is configured.
To do this open Control Panel ➜ Internet Options ➜ Advanced, and uncheck the Check for publisher’s certificate revocation option as shown below.
Uninstall Tentacles
If you get to the end of this guide without success, it can be worthwhile to completely remove the Tentacle configuration, data, and working folders, and then reconfigure it from scratch. This can be done without any impact to the applications you have deployed. Learn about manually uninstalling Tentacle. Working from a clean slate can sometimes expose the underlying problem.
Help us continuously improve
Please let us know if you have any feedback about this page.
Page updated on Thursday, August 28, 2025